
Apache OpenMeetings is an open source web conferencing application. It is written in Java and supports multiple database servers. It provides many features, such as audio and video conferencing, screen sharing, file explorer, a user moderation system, private messages and contacts, an integrated calendar for meeting plans and many more. You can also record a conferencing session. It provides SOAP/REST API and multiple plugins to easily integrate with Moodle, Jira, Joomla, Confluence and more.
Prerequisites
- A Vultr CentOS 7 server instance with at least 4GB RAM.
- A sudo user.
- A domain name pointed towards the server.
For this tutorial, we will use 192.168.1.1 as the public IP address and meetings.example.com as the domain name pointed towards the Vultr instance. Please make sure to replace all occurrences of the example IP address and domain name with the actual one.
Update your base system using the guide How to Update CentOS 7. Once your system has been updated, proceed to install Java.
Install Java
OpenMeetings is written in Java, thus it requires Java Runtime Environment (JRE) to work. Download the latest available Oracle SE JDK 8 RPM package, which includes both JRE and JDK.
wget --header 'Cookie: oraclelicense=a' http://download.oracle.com/otn-pub/java/jdk/8u161-b12/2f38c3b165be4555a1fa6e98c45e0808/jdk-8u161-linux-x64.rpmInstall the downloaded package.
sudo rpm -Uvh jdk-8u161-linux-x64.rpmIf Java has installed successfully, then you will be able to verify its version.
java -versionYou will see the following output.
[user@vultr ~]$ java -version
java version "1.8.0_161"
Java(TM) SE Runtime Environment (build 1.8.0_161-b12)
Java HotSpot(TM) 64-Bit Server VM (build 25.161-b12, mixed mode)Before we can proceed further, we will need to set up the JAVA_HOME and JRE_HOME environment variables. Find the absolute path of the JAVA executable in your system.
readlink -f $(which java)You will see a similar output.
[user@vultr ~]$ readlink -f $(which java)
/usr/java/jdk1.8.0_161/jre/bin/javaNow, set the JAVA_HOME and JRE_HOME environment variables according to the path of the Java directory.
echo "export JAVA_HOME=/usr/java/jdk1.8.0_161" >> ~/.bash_profile
echo "export JRE_HOME=/usr/java/jdk1.8.0_161/jre" >> ~/.bash_profileExecute the bash_profile file.
source ~/.bash_profileNow you can run the echo $JAVA_HOME command to ensure that the environment variable is set.
[user@vultr ~]$ echo $JAVA_HOME
/usr/java/jdk1.8.0_161Install Dependencies
Install ImageMagick and GhostScript libraries.
sudo yum -y install epel-release
sudo yum -y install ImageMagick ghostscriptImageMagick provides support to upload images and import them to the whiteboard. GhostScript enables you to upload PDFs to the whiteboard.
Verify the version of ImageMagick and GhostScript to ensure that they are installed successfully.
[user@vultr ~]$ identify -version
Version: ImageMagick 6.7.8-9 2016-06-16 Q16 http://www.imagemagick.org
Copyright: Copyright (C) 1999-2012 ImageMagick Studio LLC
Features: OpenMP
[user@vultr ~]$ ghostscript -v
GPL Ghostscript 9.07 (2013-02-14)
Copyright (C) 2012 Artifex Software, Inc. All rights reserved.Furthur, we will also need to install either Apache OpenOffice or LibreOffice on the system. Installing either of these will enable OpenMeetings to import the files in Office document formats such as .doc, .docx, .ppt, .pptx, or .xlx. In this tutorial, we will install Apache OpenOffice.
Switch to the temporary directory and download the Apache OpenOffice RPM.
cd /tmp
wget https://downloads.sourceforge.net/project/openofficeorg.mirror/4.1.5/binaries/en-US/Apache_OpenOffice_4.1.5_Linux_x86-64_install-rpm_en-US.tar.gzExtract the archive and install all the RPM packages.
tar xf Apache_OpenOffice_4.1.5_Linux_x86-64_install-rpm_en-US.tar.gz
cd en-US/RPMS
sudo rpm -Uvh *.rpm
sudo rpm -Uvh desktop-integration/openoffice4.1.5-redhat-menus-*.rpmTo check if OpenOffice is installed correctly and working, type openoffice4 -h in the command line. It will print its version and short help.
[user@vultr ~]$ openoffice4 -h
OpenOffice 4.1.5 415m1(Build:9789)
Usage: soffice [options] [documents...]
Options:
-minimized keep startup bitmap minimized.
...Install the RPMFusion repository in your system as it provides pre-built packages for FFmpeg and Sound eXchange (SoX).
sudo rpm -Uvh https://download1.rpmfusion.org/free/el/rpmfusion-free-release-7.noarch.rpmInstall FFmpeg and SoX.
sudo yum -y install ffmpeg soxFFmpeg and SoX will enable recording of the meeting. They will also help in importing media files such as .avi, .flv, .mov and .mp4 into the whiteboard. Verify the installation by checking the versions of both FFmpeg and SoX.
[user@vultr ~]$ sox --version
sox: SoX v14.4.1
[user@vultr ~]$ ffmpeg -version
ffmpeg version 2.8.13 Copyright (c) 2000-2017 the FFmpeg developers
built with gcc 4.8.5 (GCC) 20150623 (Red Hat 4.8.5-11)Install PostgreSQL
OpenMeetings supports multiple types of database servers, such as MySQL, PostgreSQL, Apache, Derby, and Oracle. In this tutorial, we will use PostgreSQL server to host the OpenMeeting database.
PostgreSQL is an object-relational database system and known for its stability and speed. The default yum repository contains an old version of PostgreSQL, so add the PostgreSQL repository for the latest version of the application into the system.
sudo yum -y install https://download.postgresql.org/pub/repos/yum/10/redhat/rhel-7-x86_64/pgdg-centos10-10-1.noarch.rpmInstall the PostgreSQL database server.
sudo yum -y install postgresql10-server postgresql10-contrib postgresql10 Initialize the database.
sudo /usr/pgsql-10/bin/postgresql-10-setup initdbStart the PostgreSQL server and enable it to start automatically at boot time.
sudo systemctl start postgresql-10
sudo systemctl enable postgresql-10Change the password for the default PostgreSQL user.
sudo passwd postgresLog in as the PostgreSQL user.
sudo su - postgresCreate a new PostgreSQL user for the OpenMeetings user.
createuser openmeetingsYou can use any username instead of openmeetings. Switch to the PostgreSQL shell.
psqlSet a password for the newly created user for the OpenMeetings database.
ALTER USER openmeetings WITH ENCRYPTED password 'DBPassword';Replace DBPassword with a secure password. Create a new database for the OpenMeetings installation.
CREATE DATABASE openmeetings OWNER openmeetings;Exit from the psql shell.
\qSwitch to the sudo user.
exitEdit the pg_hba.conf file to enable MD5 based authentication.
sudo nano /var/lib/pgsql/10/data/pg_hba.confFind the following lines and change the values in the METHOD column from ident to md5.
# TYPE DATABASE USER ADDRESS METHOD
# "local" is for Unix domain socket connections only
local all all peer
# IPv4 local connections:
host all all 127.0.0.1/32 ident
# IPv6 local connections:
host all all ::1/128 identOnce updated, the configuration will look like this.
# TYPE DATABASE USER ADDRESS METHOD
# "local" is for Unix domain socket connections only
local all all peer
# IPv4 local connections:
host all all 127.0.0.1/32 md5
# IPv6 local connections:
host all all ::1/128 md5Save the file and exit from the editor. Restart PostgreSQL so that the changes can take effect.
sudo systemctl restart postgresql-10Installing OpenMeetings
Since all the required dependencies are installed. Create a new user for OpenMeetings. Using a non-root user for running OpenMeetings is recommended for the security of the server.
sudo adduser -b /var -s /sbin/nologin openmeetings
The above command will also create the home directory of the openmeetings user in /var/openmeetings.
Check the Apache OpenMeetings download page to obtain the link to the latest available release. Download the OpenMeetings archive.
cd /tmp
wget http://www-us.apache.org/dist/openmeetings/4.0.1/bin/apache-openmeetings-4.0.1.tar.gzExtract the archive into the /var/openmeetings directory.
sudo tar xf apache-openmeetings-4.0.1.tar.gz -C /var/openmeetingsProvide ownership of the files to the OpenMeetings user we have created earlier.
sudo chown -R openmeetings:openmeetings /var/openmeetingsBefore we start the application, we will need to modify the firewall to allow ports 5080 and 1935.
sudo firewall-cmd --zone=public --permanent --add-port=5080/tcp
sudo firewall-cmd --zone=public --permanent --add-port=1935/tcp
sudo firewall-cmd --reloadYou can now start the application.
sudo su -s /bin/bash -c 'cd /var/openmeetings/ && sh red5.sh' openmeetingsYou can now access http://192.168.1.1:5080/openmeetings in your favorite browser. You will see the welcome screen with instructions to install GhostScript.
Since we have already installed GhostScript, proceed further. On next interface, you will be prompted to provide database server details. Select database type "PostgreSql" and provide your database server details that you configured during PostgreSQL installation.
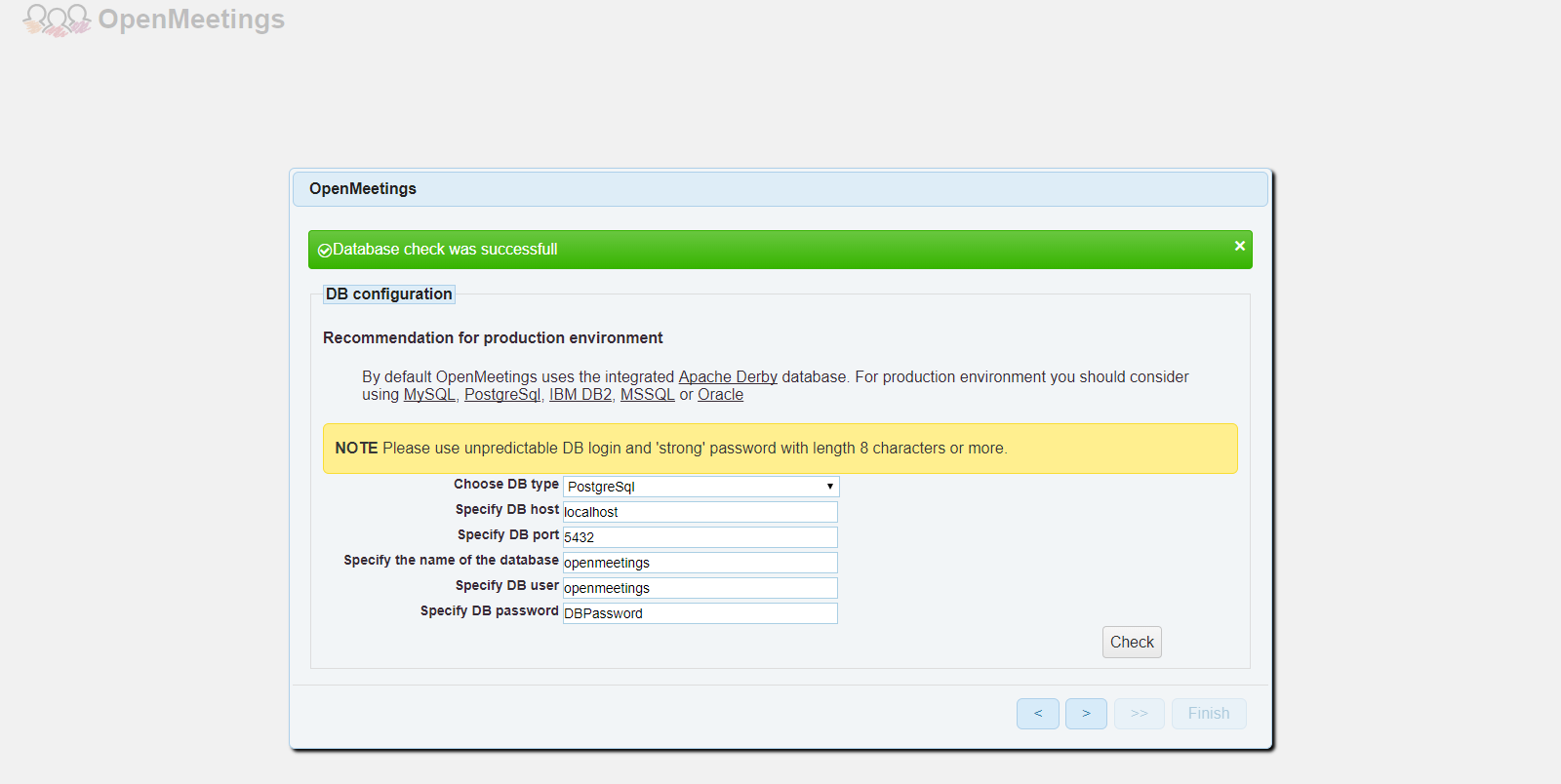
Click on the "Check" button and you should get the message: "Database check was successful". Provide your administrator account details and a group name in the next interface.
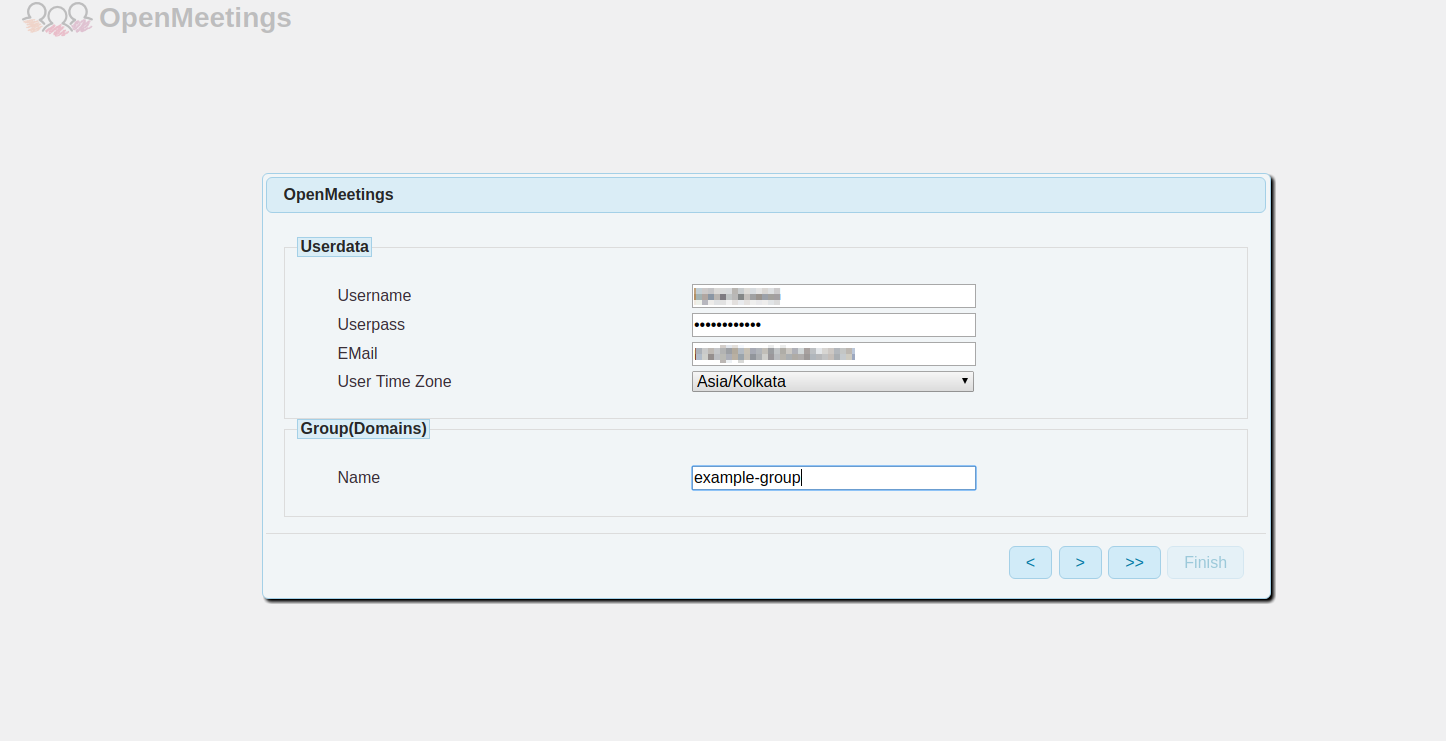
Configure the basic settings of your installation; such as to allow self-registration, email verification, and default language. Also, provide your SMTP server details. If you do not have an SMTP server ready than you can also provide the SMTP details later in the administrator dashboard.
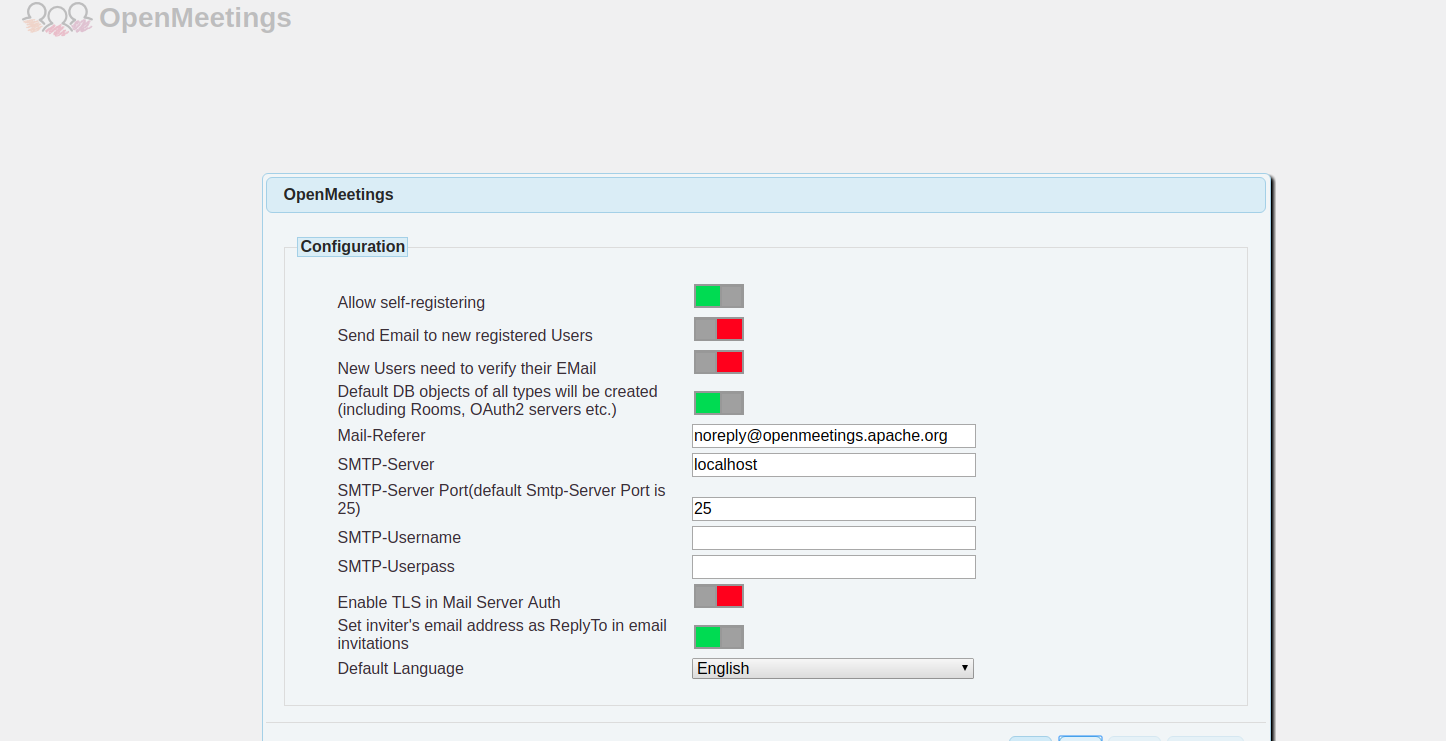
It will ask you for the path to the binaries of different applications. Provide /usr/bin as the path for ImageMagick, FFmpeg, and SoX. If the application is providing errors for the path entered, then you can use which <binary_name> to find the absolute path to the binary. For example, which ffmpeg should give you /usr/bin/ffmpeg as output. Use /opt/openoffice4 as the path to the OpenOffice binaries.
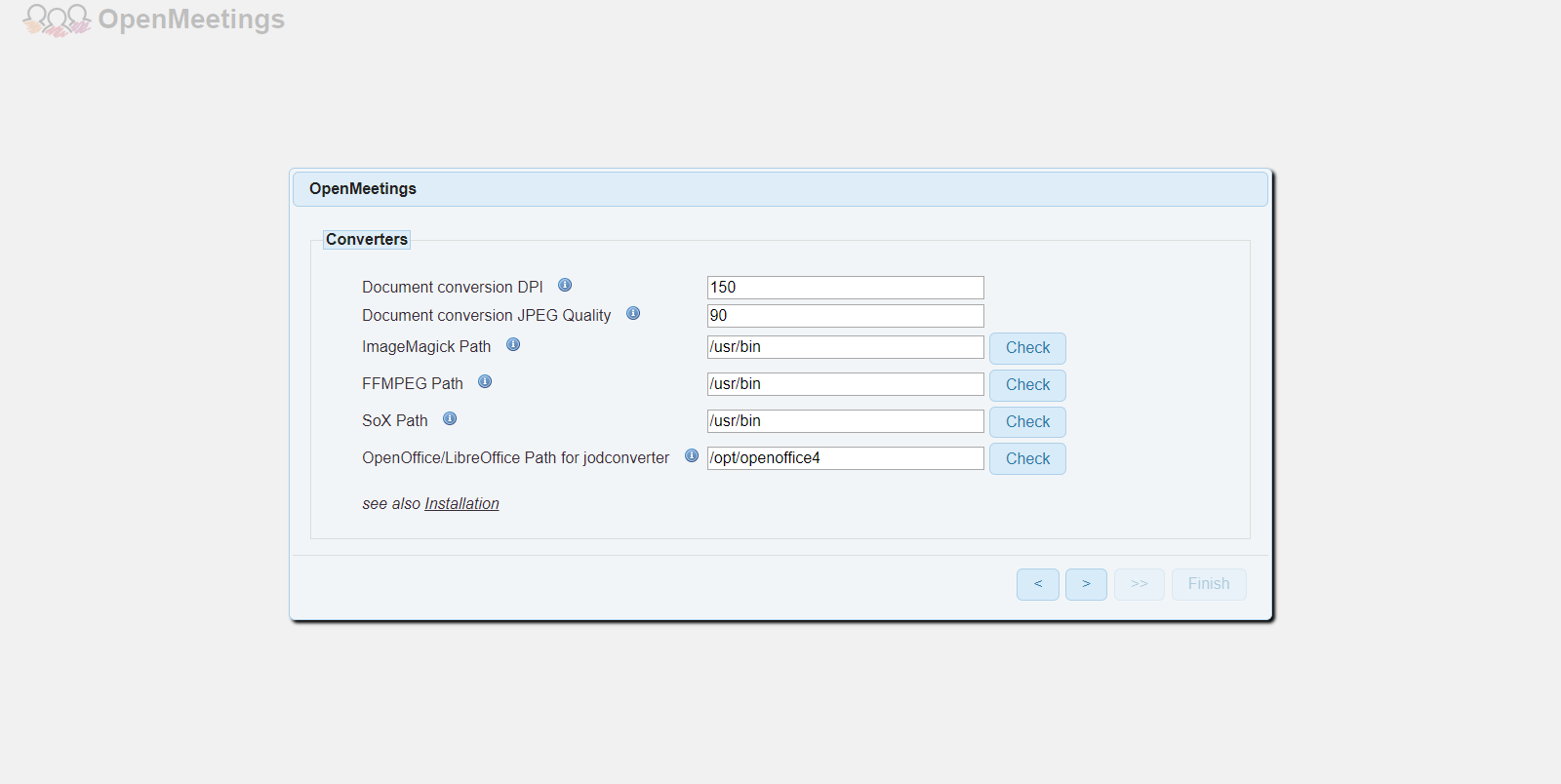
You can skip the configuration on the next interface since we are going to use the default values. Finally, click the "Finish" button to install the application and write the database.
OpenMeetings is now installed on your server. To make it more production friendly, we will setup Systemd to manage the OpenMeetings server. We will also configure Nginx with Let's Encrypt SSL as the secured reverse proxy to serve the application.
Setting up Systemd
Though we can easily start and stop the application using the command above, it is recommended to set up a Systemd service unit to manage the application. This will also ensure that the service is automatically started on boot time and failures.
Stop the OpenMeetings server either by pressing "Ctrl+C" or by killing the shell of the openmeetings user.
sudo pkill -KILL -u openmeetingsCreate a new Systemd unit file for OpenMeetings Server.
sudo nano /etc/systemd/system/openmeetings.servicePopulate the file.
[Unit]
Description=OpenMeeting Service
After=network.target
[Service]
Type=simple
User=openmeetings
WorkingDirectory=/var/openmeetings
ExecStart=/var/openmeetings/red5.sh
Restart=always
[Install]
WantedBy=multi-user.targetStart the OpenMeetings server and enable it to automatically start at boot time.
sudo systemctl start openmeetings
sudo systemctl enable openmeetingsTo check the status of the service, you can run the following.
sudo systemctl status openmeetingsYou will see a similar output.
[root@vultr openmeetings]# sudo systemctl status openmeetings
● openmeetings.service - OpenMeeting Service
Loaded: loaded (/etc/systemd/system/openmeetings.service; enabled; vendor preset: disabled)
Active: active (running) since Wed 2018-01-31 15:40:56 UTC; 38s ago
Main PID: 10522 (java)
CGroup: /system.slice/openmeetings.service
└─10522 /bin/java -Dred5.root=/var/openmeetings -Djava.security.debug=failure -Xms256m...
Jan 31 15:41:29 vultr.guest red5.sh[10522]: [INFO] [Loader:/openmeetings] org.red5.server.Serv...ngs
Jan 31 15:41:29 vultr.guest red5.sh[10522]: [INFO] [Loader:/openmeetings] org.red5.server.Serv...ngs
Jan 31 15:41:29 vultr.guest red5.sh[10522]: DEBUG 01-31 15:41:29.431 16603 343 o.a.o.c.r.Scope...se]
Jan 31 15:41:29 vultr.guest red5.sh[10522]: DEBUG 01-31 15:41:29.531 16703 124 o.a.o.c.r.Scope...ngs
Jan 31 15:41:34 vultr.guest red5.sh[10522]: DEBUG 01-31 15:41:34.421 21593 82 o.a.o.u.Version ...] -
Jan 31 15:41:34 vultr.guest red5.sh[10522]: ##################################################...###
Jan 31 15:41:34 vultr.guest red5.sh[10522]: # Openmeetings is up ... #
Jan 31 15:41:34 vultr.guest red5.sh[10522]: # 4.0.1 3795f14 2017-12-05T16... #
Jan 31 15:41:34 vultr.guest red5.sh[10522]: # and ready to use ... #
Jan 31 15:41:34 vultr.guest red5.sh[10522]: ##################################################...###
Hint: Some lines were ellipsized, use -l to show in full.Setup Nginx as Reverse Proxy
By default, OpenMeetings listens to port 5080. If the connection between the browser and server are not encrypted with SSL, then logins and other information will be sent using plain text. This might be a potential threat as someone eavesdropping on the network might obtain the information. To mitigate this issue, we will setup Nginx as the reverse proxy which will listen to the default HTTPS port and will proxy all the requests to the OpenMeetings server.
Install Nginx.
sudo yum -y install nginxStart Nginx and enable it to automatically start at boot time.
sudo systemctl start nginx
sudo systemctl enable nginxInstall Certbot, which is the client application for Let's Encrypt CA.
sudo yum -y install certbotBefore you can request the certificates, you will need to allow ports 80 and 443 or standard HTTP and HTTPS services through the firewall.
sudo firewall-cmd --zone=public --add-service=http --permanent
sudo firewall-cmd --zone=public --add-service=https --permanent
sudo firewall-cmd --reloadNote: To obtain certificates from Let's Encrypt CA, the domain for which the certificates are to be generated must be pointed towards the server. If not, make the necessary changes to the DNS records of the domain and wait for the DNS to propagate before making the certificate request again. Certbot checks the domain authority before providing the certificates.
Generate the SSL certificates.
sudo certbot certonly --webroot -w /usr/share/nginx/html -d meetings.example.comThe generated certificates are likely to be stored in /etc/letsencrypt/live/meetings.example.com/. The SSL certificate will be stored as fullchain.pem and private key will be stored as privkey.pem.
Let's Encrypt certificates expire in 90 days, hence it is recommended to set up auto-renewal of the certificates using Cron jobs.
Open the cron job file.
sudo crontab -eAdd the following line at the end of the file.
30 5 * * * /usr/bin/certbot renew --quietThe above cron job will run every day at 5:30 AM. If the certificate is due for expiry, it will automatically be renewed.
Now, change the Nginx default configuration file to take out the default_server line.
sudo sed -i 's/default_server//g' /etc/nginx/nginx.confCreate a new configuration file for OpenMeetings Server.
sudo nano /etc/nginx/conf.d/meetings.example.com.confPopulate the file.
server {
listen 80;
server_name meetings.example.com;
return 301 https://$host$request_uri;
}
server {
listen 443;
server_name meetings.example.com;
ssl_certificate /etc/letsencrypt/live/meetings.example.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/meetings.example.com/privkey.pem;
ssl on;
ssl_session_cache builtin:1000 shared:SSL:10m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4;
ssl_prefer_server_ciphers on;
access_log /var/log/nginx/openmeetings.access.log;
location / {
proxy_pass http://localhost:5080;
proxy_set_header host $host;
proxy_http_version 1.1;
proxy_set_header upgrade $http_upgrade;
proxy_set_header connection "upgrade";
}
}Check for errors in the new configuration file.
sudo nginx -tIf you see the following output, the configuration is error free.
[user@vultr ~]$ sudo nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successfulIf you have received some kind of error, make sure to double check the path to the SSL certificates. Restart the Nginx web server to implement the change in configuration.
sudo systemctl restart nginxBefore you can start using the application on the SSL secured site, you will need to make a configuration change in OpenMeetings. Login to your OpenMeetings administrative dashboard and navigate to "Administration >> Configuration". In the table of ID, key and value; find application.base.url. Change its value to https://meetings.example.com according to your domain name. Save the configuration by clicking the save icon above.
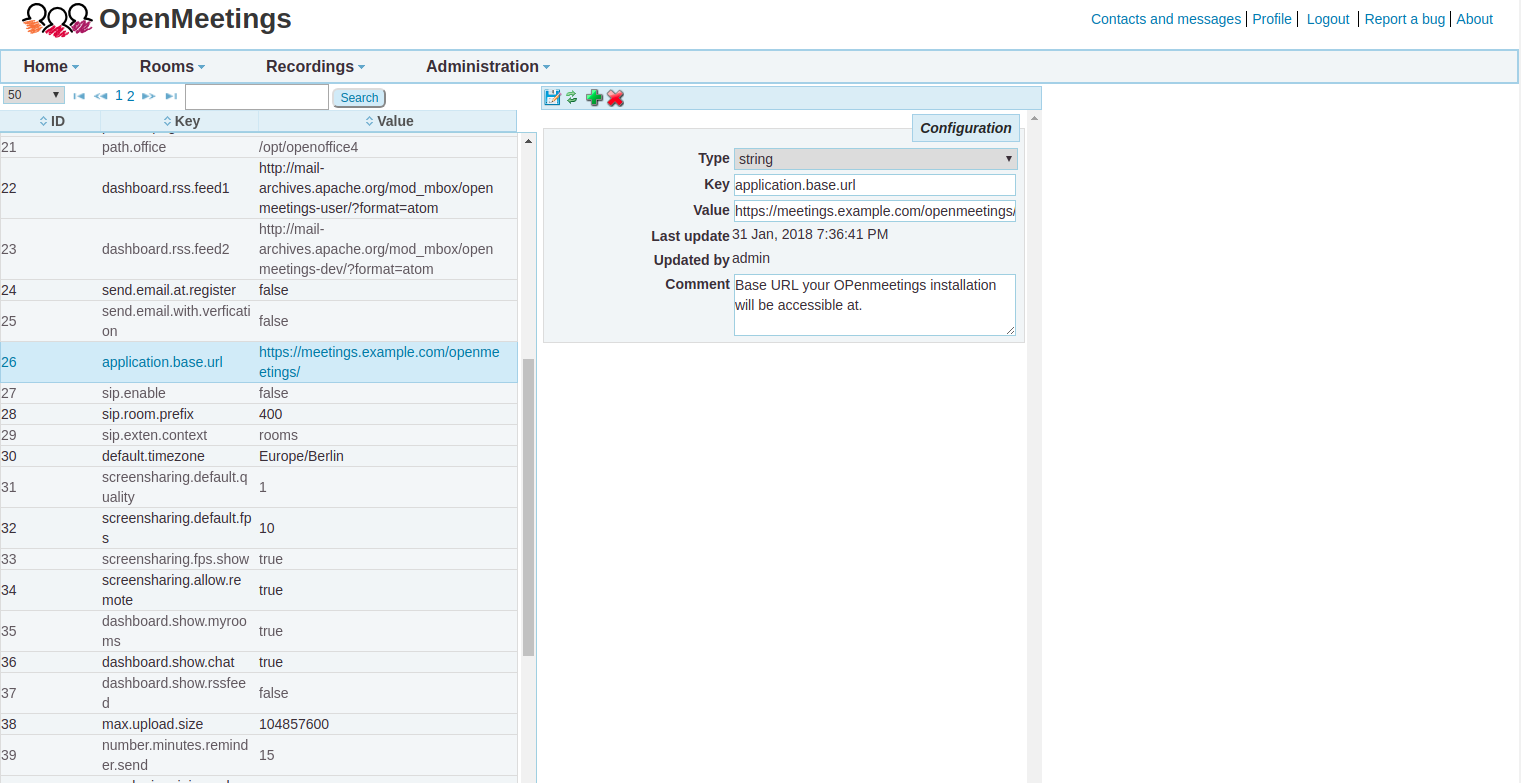
Restart the OpenMeetings service.
sudo systemctl restart openmeetingsNow, you can browse to https://meetings.example.com using your favorite web browser and log in to use the application.
Congratulations, Apache OpenMeetings is now installed on your server. You can invite your friends and start using OpenMeetings for online conferences.
No comments yet.