How to Use SSH with Vultr Servers

Introduction
SSH is a protocol that allows you to connect to Linux or Unix-based servers from the remote system. OpenSSH is a connectivity tool that uses the SSH protocol to communicate between the client and server using the secure shell. This guide explains how to SSH into your Vultr server with a password or use SSH keys using OpenSSH. It also describes how to generate SSH keys and add them to the server manually.
How to Connect with a Password
To connect to the server using the SSH client and a password, open the command prompt on your local workstation and execute the following command. Substitute the example IP address with the server's IP address, which you'll find on the server information page in the Vultr customer portal.
$ ssh root@192.0.2.123SSH shows a warning to confirm the authenticity of the server. Type Yes and press Enter. You'll see the password prompt. Type the password and press Enter.
Note: Passwords will not be visible when you type.
Now, you'll be logged into the server, and you can use the commands to interact with the server.
What is an SSH Key Pair
SSH key pair contains a public key and a private key. The public key is stored on the server, and the private key is stored on the local machine that will be used for connecting to the remote server. Both keys are necessary to SSH into a server using the SSH keys.
How to Generate Keys on Windows, Linux, Mac
ssh-keygen utility can be used to generate SSH keys.
How to use the ssh-keygen Command
Use the below command to generate the key pair in Windows, Linux, and Mac.
ssh-keygen -t ed25519 -C email@example.comWhere,
ssh-keygen- Command to generate the SSH key pair-t- Flag to specify the key typeed25519- Type of the key to be generated.ed25519is recommended as its more secure than RSA type keys-C- Flag to specify the comment for the keyemail- Comment to be added in the key. This comment will be appended at the end of the public key string. It'll help identify the keys when more public keys are available on your server (more on this topic later).
Generating Keys on Windows
Launch the command prompt and use the below command to generate the SSH key pair.
C:\users\username> ssh-keygen -t ed25519 -C email@example.comThe system prompts you to enter the location for generating the keys. The default value is shown in the brackets as (C:\Users\Username/.ssh/id_ed25519).
Note: It is recommended to use this directory. Because while logging in, SSH will look for the keys in the default directory. If you use directories other than the default directory, you need to specify the key location explicitly.
Press Enter to use the default location.
Generating public/private ed25519 key pair.
Enter file in which to save the key (C:\Users\username/.ssh/id_ed25519):The system shows the prompt to enter the passphrase for the key. You can enter a passphrase if you wish, or you can press Enter to create keys without a passphrase. If you choose to enter a passphrase, you need to use it every time while logging in using this key.
Enter passphrase (empty for no passphrase):After confirming the passphrase, the key is generated and stored in the default location, and the below message is shown.
Your identification has been saved in C:\Users\username/.ssh/id_ed25519.
Your public key has been saved in C:\Users\username/.ssh/id_ed25519.pub.
The key fingerprint is:
SHA256:W6ceE1mGIi87YjD9BEUoROg3Aie/fOZMr1c+qOSD8Wk email@example.com
The key's randomart image is:
+--[ED25519 256]--+
| +o oo |
+----[SHA256]-----+Generating Keys on Linux
Launch the Linux shell and use the below command to create an SSH keypair.
$ ssh-keygen -t ed25519 -C email@example.comThe system prompts you to enter the location for the keys. The default value is shown in the brackets as (/home/username/.ssh/id_ed25519)
Note: It is recommended to use this directory. Because while logging in, SSH will look for the keys in the default directory. If you use directories other than the default directory, you need to specify the key location explicitly.
Press Enter to use the default location.
Generating public/private ed25519 key pair.
Enter file in which to save the key (C:\Users\username/.ssh/id_ed25519):The system shows the prompt to enter the passphrase for the key. You can enter a passphrase if you wish, or you can press Enter to create keys without a passphrase. If you choose to enter a passphrase, you need to use it every time while logging in using this key.
Enter passphrase (empty for no passphrase):After confirming the passphrase, the key is generated and stored in the default location, and the below message is shown.
Your identification has been saved in /home/ubuntu/.ssh/id_ed25519
Your public key has been saved in /home/ubuntu/.ssh/id_ed25519.pub
The key fingerprint is:
SHA256:c0hYyBV+e1vY7DUVage/3nYk4z9DvxzrLmsiek7dkZE email@example.com
The key's randomart image is:
+--[ED25519 256]--+
| . o+. . . |
+----[SHA256]-----+
| o+ = .|Generating Keys on Mac
Launch the terminal and use the below command to generate the SSH key pair.
% ssh-keygen -t ed25519 -C email@example.comThe system prompts you to enter the location for generating the keys. The default value is shown in the brackets as (/Users/Username/.ssh/id_ed25519).
Note: It is recommended to use this directory. Because while logging in, SSH will look for the keys in the default directory. If you use directories other than the default directory, you need to specify the key location explicitly.
Press Enter to use the default location.
Generating public/private ed25519 key pair.
Enter file in which to save the key (/Users/Username/.ssh/id_ed25519):The system shows the prompt to enter the passphrase for the key. You can enter a passphrase if you wish, or you can press Enter to create keys without a passphrase. If you choose to enter a passphrase, you need to use it every time while logging in using this key.
Enter passphrase (empty for no passphrase):After confirming the passphrase, the key is generated and stored in the default location, and the below message is shown.
Your identification has been saved in /Users/Username/.ssh/id_ed25519.
Your public key has been saved in /Users/Username/.ssh/id_ed25519.pub.
The key fingerprint is:
SHA256:W6ceE1mGIi87YjD9BEUoROg3Aie/fOZMr1c+qOSD8Wk email@example.com
The key's randomart image is:
+--[ED25519 256]--+
| +o oo |
+----[SHA256]-----+How to Add a Key to an Existing Server
The SCP command is used to copy a file to the remote server. Your public SSH key must be copied to the server to enable SSH authentication. You can use the scp command to copy the public key to the remote server.
Launch the command prompt or the Linux shell and execute the below command to copy the public key.
C:\users\username> scp C:\Users\username\.ssh\id_ed25519.pub example_user@192.0.2.123:/home/example_user Where,
SCP- Command to copy the fileC:\Users\username\.ssh\id_ed25519.pub- Generated public key locationexample_user- Username of the server to which the file needs to be copied. You need to have access to this server192.0.2.123- IP Address of the server/home/example_user- Target folder location on the server
The file is copied to the directory. Now, you need to copy the key to the authorized_keys file and enable SSH authentication. Log in to your newly created Vultr server and navigate to the user's home directory using the below command.
$ cd /home/example_user/ Make a directory .ssh if it's not already existing using the below command.
$ mkdir .sshNavigate to the .ssh folder.
$ cd .sshCreate a authorized_keys that will store the public key in the server using the below command.
$ touch authorized_keysThe touch command will create a file only if it doesn't exist.
Once the file is created, copy the content of the public key to the authorized_keys file using the cat command as shown below.
$ cat /home/example_user/id_ed25519.pub >> authorized_keysThe keys are placed in the appropriate location.
Enabling SSH Keys Authentication
SSH Authentication methods are configured in the file called sshd_config.
To enable the authentication using SSH keys, navigate to the directory /etc/ssh/ using the below command.
$ cd /etc/ssh Open the file sshd_config using the below command.
$ sudo nano sshd_configIn the file, find and uncomment the following two lines.
PubkeyAuthentication yes
AuthorizedKeysFile .ssh/authorized_keys .ssh/authorized_keys2Setting the PubkeyAuthentication parameter to yes enables authentication using the public keys. And the AuthorizedKeysFile parameter specifies the location of the public key. Now, the keys are added to the existing server. You can SSH into the server using the public key using the steps defined in the next section.
How to Connect with a Key
The OpenSSH client provides the ssh command to establish an SSH connection into the server. Launch the command prompt and use the below command to SSH into a server using the SSH keys.
C:\users\username> ssh example_user@192.0.2.123Where,
ssh- command to establish a connectionexample_user- Username to use to make a connection192.0.2.123- IP address of the server
This command will use the private key in the default ssh directory (./users/.ssh) of your local machine. If the public and private keys match correctly, the SSH connection will be established, and you can communicate with the server.
How to Deploy a New Server with a Key
To deploy a new server with an SSH key, you need to create an SSH key in the Vultr Dashboard. Follow the below steps to add an SSH key to your Vultr account.
Log in to the Customer Portal.
Click your name in the upper-right, then select SSH Keys from the dropdown menu.
Click the blue "plus sign" button to add a key.
Enter a descriptive name for the key.
Paste the public key into the SSH Key field.
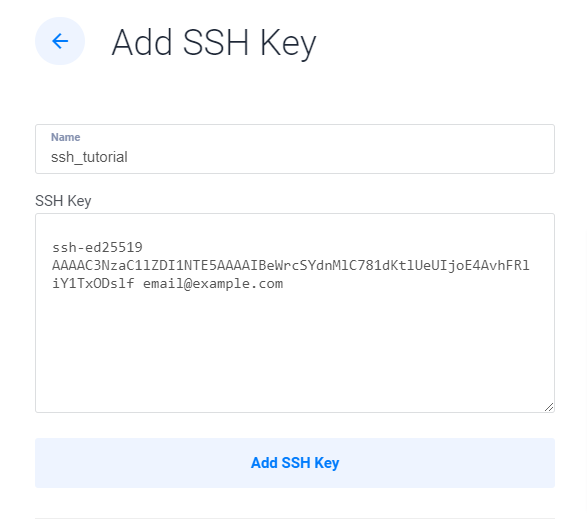
Click the Add SSH key button to create an SSH key.
The SSH key will be added, and you'll be able to select this SSH key in the SSH Keys section while launching a new server.
More Information
For more information, see our other guides:
- How to Generate SSH Keys
- Deploy a New Server with an SSH Key
- How to Add and Delete SSH Keys
- Use an SSH Key for Non-root Users
- Connect to a Server Using an SSH Key
- How To Connect to your Vultr Cloud Server with SSH, RDP, or SFTP