Introduction
Iptables is a built-in command-line utility that performs packet filtering functionalities using the Linux Kernel Netfilter firewall framework. It controls incoming and outgoing network traffic by matching network packets with available chain rules on the server. Iptables uses a hierarchical rule execution format which includes tables, chains, and rules to filter network traffic on the server.
This article explains how to set up firewall policies using iptables on a Vultr Cloud Server. You will set up basic traffic filtering rules with target decisions to accept, drop, or reject network packets on the server.
Prerequisites
- Deploy a Vultr Linux Server to use as the workstation.
- Access the server using SSH as a non-root user with sudo privileges.
Set Up Firewall Policies
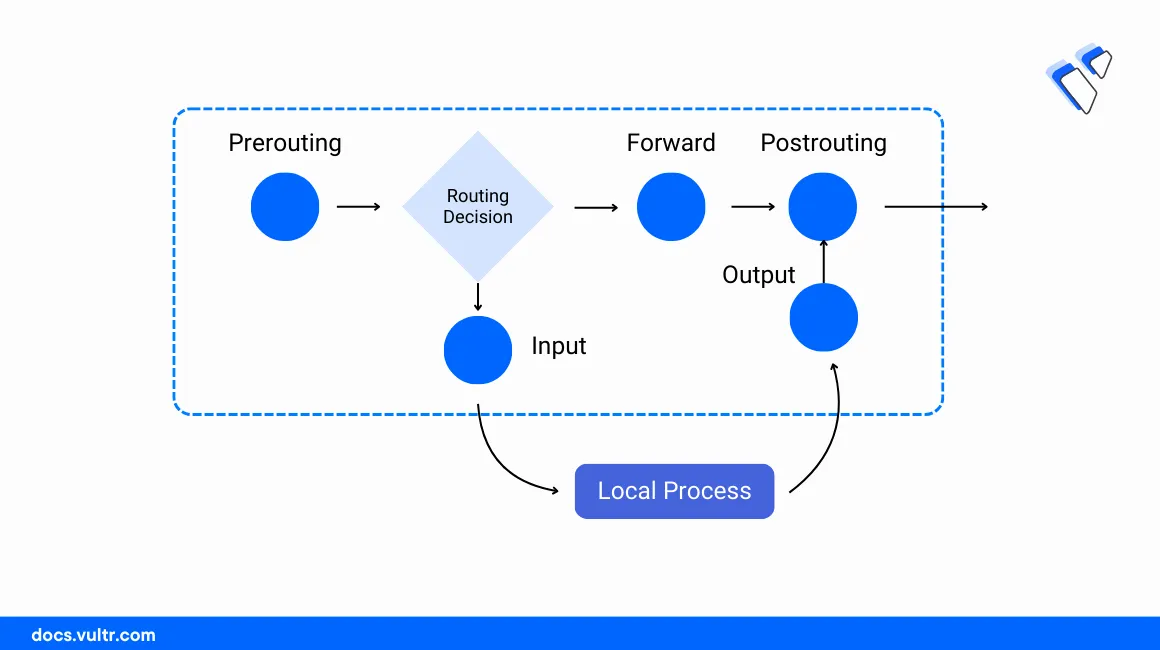
Iptables can filter network packets based on the target table and chain rules. Below are the main tables referenced by iptables.
- Filter Table: Contains packet filtering rules that either allow or deny packets to continue to the intended destination.
- NAT Table: Contains network packet modification rules that translate specific source addresses to your server network address for forwarding purposes on the server.
- Raw Table: Enables access to network packets before the Linux Kernel state tracking process.
- Security Table: Sets the internal host SELinux security context on network packets.
- Mangle Table: Contains rules that alter network packet headers and information such as the time to live (TTL) value.
To configure firewall policies, iptables uses the following built-in chain rules to filter network traffic.
INPUT: Captures incoming network packets on the server. Rules for incoming traffic.OUTPUT: Captures outgoing network packets.FORWARD: Forwards network packets routed within the server.
View all available iptables rules on the server.
console$ sudo iptables -L
Output:
Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destinationFollow the sections below to set up example firewall policies using iptables.
Allow Incoming Network Requests
Allow connection requests to the loopback interface
127.0.0.1.console$ sudo iptables -A INPUT -i lo -j ACCEPT
The above rule enables incoming connection requests to the localhost loopback interface. Within the command:
-A: Adds the rule to the filter table INPUT chain.-i lo: Applies the rule to the loopback (lo) interface.-j ACCEPT: Accepts matching network packets without any extra processing.
Allow already established and two-way network connections on the server.
console$ sudo iptables -A OUTPUT -m conntrack --ctstate ESTABLISHED -j ACCEPT
The above rule accepts incoming network requests to already established connections and related connections in the form of two-way traffic.
Allow incoming connections to a specific network port. For example, allow incoming SSH connection requests to the server TCP port
22from your public IP address subnet192.0.2.0/30.console$ sudo iptables -A INPUT -p tcp -s 192.0.2.0/30 --dport 22 -m conntrack --ctstate NEW,ESTABLISHED -j ACCEPT
Allow incoming connections from one network interface to another. For example, allow network requests from the
enp1s0interface to theenp8s0interface.console$ sudo iptables -A FORWARD -i enp1s0 -o enp8s0 -j ACCEPT
The above command forwards connection requests from one interface to another. However, additional static routing or NAT processing is required to route connections between hosts on the different networks.
Allow Outgoing Network Requests
Allow all outgoing network traffic from the server without any port or address restrictions.
console$ sudo iptables -A OUTPUT -j ACCEPT
Allow outgoing network traffic from the loopback interface
127.0.0.1.console$ sudo iptables -A OUTPUT -o lo -j ACCEPT
Allow established outgoing network connections that match an already established incoming connection.
console$ sudo iptables -A OUTPUT -m conntrack --ctstate ESTABLISHED -j ACCEPT
Block IP Addresses and Network Requests
Block IP network connections that originate from a specific IPV4 address. For example,
192.0.2.50.console$ sudo iptables -A INPUT -s 192.0.2.50 -j DROP
The above command blocks the network IP
192.0.2.50from accessing any resources on the server.Block network connections to a specific server interface. For example, block the IP
192.0.2.30from accessing the internalenp8s0in any way.console$ sudo iptables -A INPUT -i enp8s0 -s 192.0.2.30 -j DROP
Block IP access to specific network ports from a specific address range. For example,
10.10.10.0/24.console$ sudo iptables -A INPUT -p tcp -m multiport --dports 22,5901 -s 10.10.10.0/24 -j DROP
Block all incoming network requests that don't match any allowed rules.
console$ sudo iptables -A INPUT -j DROP
Delete iptables Rules
Depending on your server network requests, you can delete specific iptables rules or modify the existing entries to match your needs. For example, if a specific IP address cannot access the server, you can delete the IP block rule or modify the existing rules to your needs.
View the available iptables rules and identify the target rule to delete.
console$ sudo iptables -L
Append the -D option instead of -A on your original iptables rule to delete the target entry. For example, delete the IP blocking rule for the host address
192.0.2.50.console$ sudo iptables -D INPUT -s 192.0.2.50 -j DROP
Enable NAT and Port Forwarding
Enable NAT resolution through the public interface
enp1s0.console$ sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
The above NAT rule translates all network requests to the
enp1s0IP address. For example, hosts on theenp8s0network route to external networks using theenp1s0interface IP. Within the above command:-t nat: Applies the rule to the NAT table.-A POSTROUTING: Appends rule to the POSTROUTING chain within the NAT table.-o eth0: Sets the target network interface to translate requests.-j MASQUERADE: Enables modification of the source IP address to match the external interface IP.
Forward traffic from a specific port such as
80to an interface such asenp8s0.console$ sudo iptables -t filter -A PREROUTING -i enp8s0 -p tcp --dport 8080 -j ACCEPT
Forward traffic from a specific port to a single destination IP address such as
192.168.1.1using dynamic NAT.console$ sudo iptables -t nat -A PREROUTING -i enp8s0 -p tcp --dport 8080 -j DNAT --to-destination 192.168.1.100
Log Iptables Rules
Log all dropped network packets for debugging purposes with the prompt
Dropped iptables packets.console$ sudo iptables -A INPUT -j LOG --log-prefix "Dropped iptables packets:"
Log all unknown network packets with the prompt
Unknown network packets:.console$ sudo iptables -A INPUT -j LOG --log-prefix "Unknown network packets:"
View the system log file
/var/log/syslogto verify the iptables log entries that match your rules.console$ sudo cat /var/log/syslog
Permanently Save Iptables Rules
Install the
iptables-persistentpackage.console$ sudo apt install iptables-persistent
Save the iptables rules.
console$ sudo netfilter-persistent save
Conclusion
You have set up firewall policies using iptables on a Vultr Linux Server and configured multiple rules to filter network requests. iptables offers extended functionalities that filter multiple network requests on the server depending on the request type and origin. For more information and iptables commands, visit the utility manual page using the command man iptables.