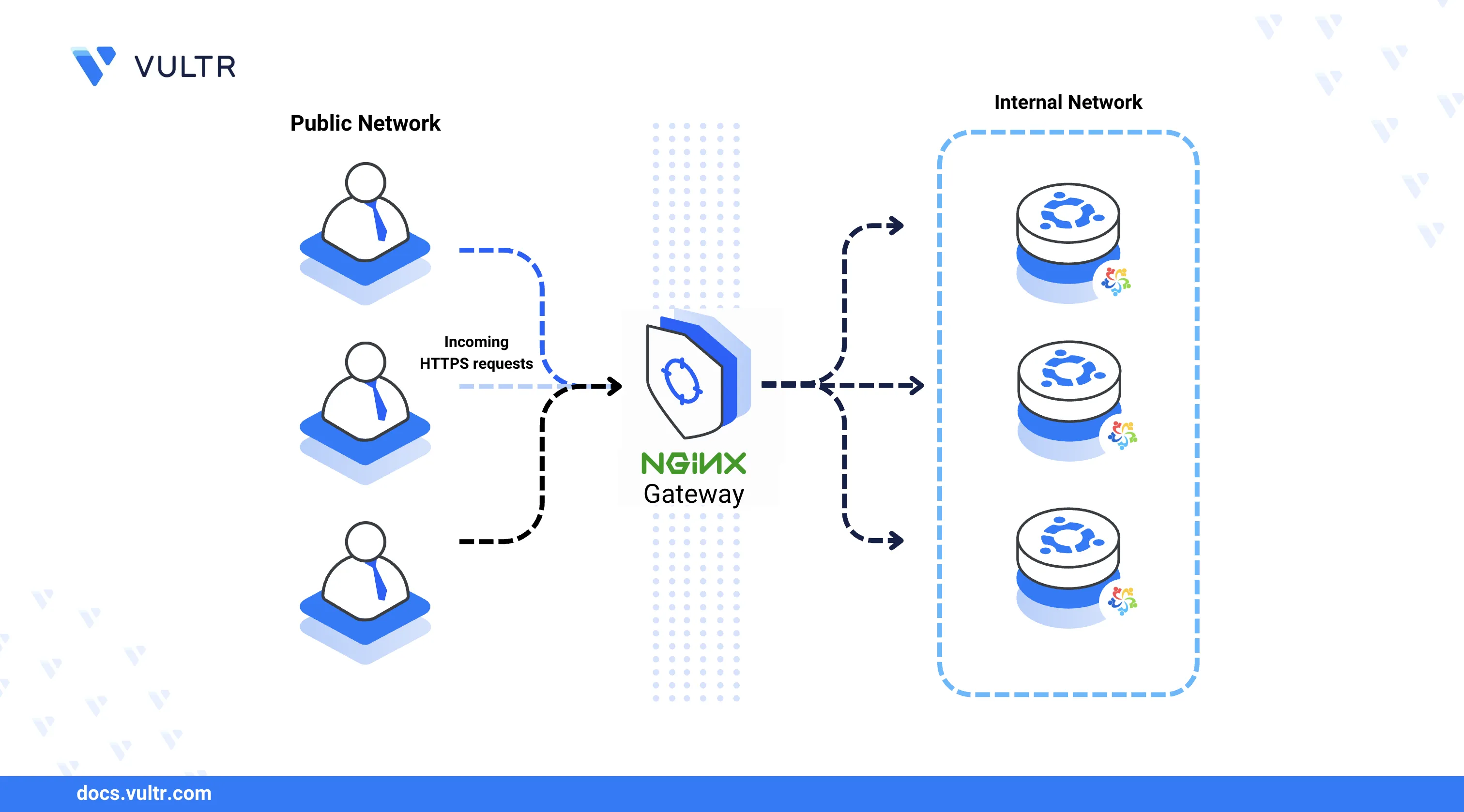
Nginx is a high-performance, open-source web server that functions as a reverse proxy, load balancer, and HTTP cache. To deploy it on a stable enterprise-grade platform, you can install Nginx Web Server on AlmaLinux 9. It easily handles static and dynamic content and works well with technologies such as PHP and database servers.
In this article, you'll learn how to install and configure Nginx on AlmaLinux 9. The steps include installing Nginx, managing the system service, setting up a custom server block (virtual host), and enabling HTTPS with Let's Encrypt.
Prerequisites
Before you begin, you need to:
- Have access to an AlmaLinux 9 instance as a non-root user with sudo privileges.
Install Nginx on AlmaLinux 9
You can install Nginx on AlmaLinux from the default DNF package sources. It's available using the nginx package name. Use the following steps to update the DNF package manager and install Nginx.
Update system packages.
console$ sudo dnf update
Install the Nginx web server.
console$ sudo dnf install nginx -y
Check that Nginx is installed correctly.
console$ sudo nginx -v
Output:
nginx version: nginx/1.20.1Start the Nginx service.
console$ sudo systemctl start nginx
Enable HTTP traffic in the firewall.
console$ sudo firewall-cmd --permanent --add-service=http
Run the following command to install Firewalld if it's not installed and allow SSH connections.
console$ sudo dnf install firewalld -y && sudo firewall-cmd --permanent --add-service=ssh
Start Firewalld if it's not running.
console$ sudo systemctl start firewalld
Apply firewall changes.
console$ sudo firewall-cmd --reload
Verify that Nginx is working in a browser.
http://server-ip-address
Manage the Nginx System Service
Nginx installs a systemd service by default. Use the following steps to manage the service and ensure it runs consistently on your server.
Enable Nginx to start on boot.
console$ sudo systemctl enable nginx
Start Nginx if it isn't already running.
console$ sudo systemctl start nginx
Verify the Nginx system service and confirm that it's running.
console$ sudo systemctl status nginx
Output:
● nginx.service - The nginx HTTP and reverse proxy server Loaded: loaded (/usr/lib/systemd/system/nginx.service; enabled; preset: disabled) Active: active (running) since Sun 2025-03-30 23:12:44 UTC; 1min 33s ago Main PID: 52297 (nginx) Tasks: 2 (limit: 5716) Memory: 2.0M CPU: 36ms CGroup: /system.slice/nginx.service ├─52297 "nginx: master process /usr/sbin/nginx" └─52298 "nginx: worker process"Reload Nginx to apply new configuration changes.
console$ sudo systemctl reload nginx
Restart the Nginx service.
console$ sudo systemctl restart nginx
Create Nginx Virtual Host Configurations (Server Blocks)
Nginx virtual host configurations include the server name, administrator, and the backend web application information. The default.d and conf.d directories contain virtual host configurations for Nginx on AlmaLinux by default unless changed. Follow these steps to create a custom server block with your own HTML content.
Verify the Nginx system service and confirm that it's running.
console$ sudo systemctl status nginx
Set up the document root and create sample content.
console$ sudo mkdir /usr/share/nginx/example && sudo nano /usr/share/nginx/example/index.html
Enter the following HTML application code in the
index.htmlfile.html<html> <body> <h1>Sample HTML Application</h1> <p>Powered by the Nginx Web Server </p> </body> </html>
Save the file and exit the text editor.
The HTML application displays when the Nginx web server loads all supported files for display in a web browser.
Create a new server block file.
console$ cd /etc/nginx/conf.d/ && sudo nano example-host.conf
Enter the following Nginx configurations into the
example-host.conffile. Replaceexample.comwith your domain.iniserver { listen 80; listen [::]:80; server_name example.com; root /usr/share/nginx/example; index index.html index.htm; access_log /var/log/nginx/example.com_access.log; error_log /var/log/nginx/example.com_error.log; location / { try_files $uri $uri/ =404; } }
Save the file and exit the text editor.
The Nginx virtual host configuration serves web application files from the
/usr/share/nginx/exampledirectory using theexample.comdomain.Test the Nginx configuration syntax for errors.
console$ sudo nginx -t
Output:
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successfulReload Nginx to apply the configuration changes.
console$ sudo systemctl reload nginx
Test access to your domain and confirm that the web application loads.
http://your-domain.com/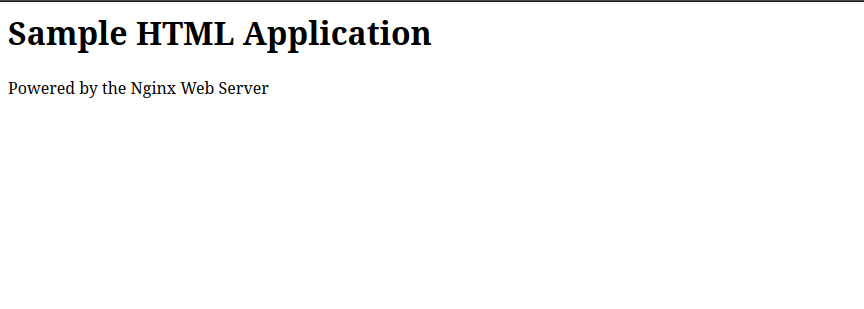
/etc/nginx.conf file. Remove the server block to disable it.
Secure the Nginx Web Server
Nginx delivers web applications using HTTP by default unless specified in your virtual host configurations. HTTPS provides encryption between the Nginx and a client's web browser, ensuring secure connections to the web server. This section walks you through installing Certbot, configuring HTTPS, and adjusting SELinux and firewall settings.
Install the EPEL repository, which includes the Certbot tool.
console$ sudo dnf install epel-release -y
Update your system packages.
console$ sudo dnf update
Install Certbot with Nginx plugin support.
console$ sudo dnf install python3-certbot-nginx -y
Request an SSL certificate using Certbot. Replace
example.comandadmin@example.comwith your actual domain and email address.console$ sudo certbot --nginx --domain example.com --email admin@example.com --agree-tos
ReplaceNoteexample.comwith your real domain name. If you don't have one, consider using a test domain or skip the SSL setup.Reload Nginx to apply the HTTPS configuration.
console$ sudo systemctl reload nginx
Test the Nginx configuration for syntax errors.
console$ sudo nginx -t
Output:
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successfulAllow HTTPS traffic through the firewall.
console$ sudo firewall-cmd --permanent --add-service=https
Optionally, remove HTTP access if you want to enforce HTTPS-only.
console$ sudo firewall-cmd --permanent --remove-service=http
Reload Firewalld to apply the new rules.
console$ sudo firewall-cmd --reload
Check the status of SELinux to ensure it's enabled.
console$ sestatusOutput:
SELinux status: enabled SELinuxfs mount: /sys/fs/selinuxInstall the required SELinux management utilities for the
semanagecommand:console$ sudo dnf install policycoreutils-python-utils -y
This ensures the
semanagetool is available to manage SELinux contexts.Update SELinux file context rules, enabling Nginx to read files in your custom directory.
console$ sudo semanage fcontext -a -t httpd_sys_content_t "/usr/share/nginx/example(/.*)?"
The SELinux
httpd_sys_content_tcontext allows Nginx to access files in multiple directories after installation. Allowing access to web application directories enables Nginx to read configurations and application files.Apply the new SELinux context.
console$ sudo restorecon -Rv /usr/share/nginx/example/
Output:
Relabeled /usr/share/nginx/example from unconfined_u:object_r:usr_t:s0 to unconfined_u:object_r:httpd_sys_content_t:s0 Relabeled /usr/share/nginx/example/index.html from unconfined_u:object_r:usr_t:s0 to unconfined_u:object_r:httpd_sys_content_t:s0Access your domain in a web browser using HTTPS to verify that the certificate is working.
https://example.com
Conclusion
You’ve now set up Nginx on AlmaLinux 9, configured it to serve static web content, and secured it with HTTPS and SELinux rules. Nginx is a flexible and high-performance web server that can easily scale to support dynamic web apps, backend integrations like PHP or databases, and production-grade deployments. From here, you can extend your setup by adding reverse proxy rules, enabling load balancing, or integrating with application stacks like Laravel, Flask, or Node.js.