How to Install Podman on Debian 12
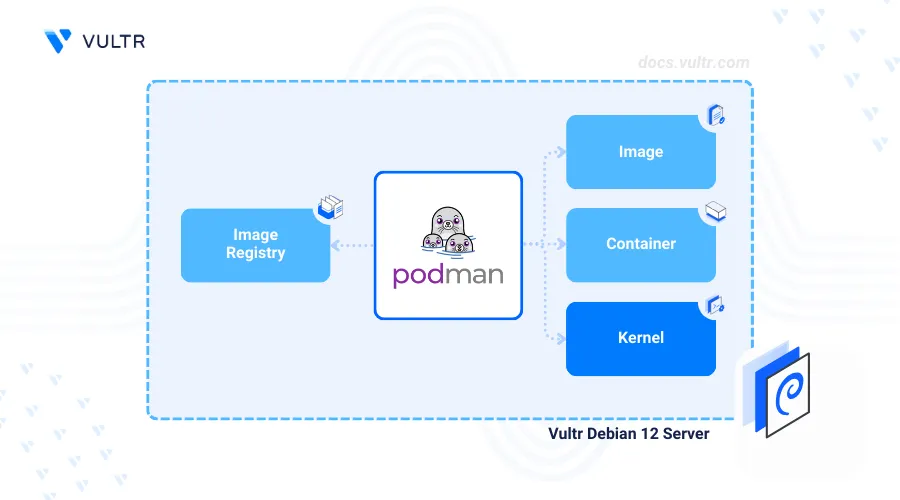
Introduction
Podman also known as Pod Manager is an open-source, daemonless container engine used to build, manage, and run Open Container Initiative (OCI) containers. Podman does not require a background daemon process making it suitable for environments such as production environments and CI/CD pipelines with improved resource usage.
This article explains how to install Podman on Debian 12 to build and run containerized applications on the server.
Prerequisites
Before you begin:
- Deploy a Debian 12 instance on Vultr.
- Create a new Vultr container registry to store your container images.
- Access the server using SSH as a non-root user with sudo privileges.
Install Podman
Podman is available in the default package repositories on Debian 12. Follow the steps below to install the latest Podman package using the APT package manager.
Update the server's package index.
console$ sudo apt update
Install Podman.
console$ sudo apt install podman -y
View the installed Podman version on your server.
console$ sudo podman --version
Output:
podman version 4.3.1
Manage the Podman System Service
Podmans uses two linked service profiles to run on a server, podman.service and podman.socket. podman.service enables access to Podman CLI and interaction with the Podman engine to run container management commands. podman.socket enables remote access to the application API, and integrates Podman with other container development tools. Follow the steps below to manage the Podman system service and enable the application to run on your server.
Enable the Podman system service to automatically start at boot.
console$ sudo systemctl enable podman
Start the Podman service.
console$ sudo systemctl start podman
View the
podman.socketservice status and verify that it's running.console$ sudo systemctl status podman.socket
Output:
● podman.socket - Podman API Socket Loaded: loaded (/lib/systemd/system/podman.socket; enabled; preset: enabled) Active: active (listening) since Sun 2024-07-28 23:57:33 UTC; 4min 11s ago Triggers: ● podman.service Docs: man:podman-system-service(1) Listen: /run/podman/podman.sock (Stream) CGroup: /system.slice/podman.socketView the
podman.servicestatus and verify that it's triggered by thepodman.socketservice.console$ sudo systemctl status podman.service
Output:
○ podman.service - Podman API Service Loaded: loaded (/lib/systemd/system/podman.service; enabled; preset: enabled) Active: inactive (dead) since Sun 2024-07-28 23:58:57 UTC; 2min 8s ago Duration: 5.037s TriggeredBy: ● podman.socketStop the Podman service.
console$ sudo systemctl stop podman
Restart the Podman service.
console$ sudo systemctl restart podman
Deploy Containerized Applications using Podman
Podman supports multiple image sources and registries to pull and run container images on your server. The /etc/containers/registries.conf configuration file includes registry information used by Podman to find container images. Podman uses default registries such as Docker Hub, quay.io, and registry.fedoraproject.org if the configuration file does not include any registry sources. Follow the steps below to deploy a containerized HTTP application using Podman using the default registry sources.
Pull the latest Apache HTTP server container image from Docker Hub using Podman CLI.
console$ sudo podman pull docker.io/httpd
Your output should be similar to the one below when successful.
//... Writing manifest to image destination Storing signatures b21577b6946fec9df0eaa3c21748d361bc19742ddb6185a4201baa4200fb35faList all Podman images and verify that the new container is available on your server.
console$ sudo podman images
Output:
REPOSITORY TAG IMAGE ID CREATED SIZE docker.io/library/httpd latest b21577b6946f 22 hours ago 152 MBDeploy a new containerized application using the
httpdimage and expose it on the localhost port8080.console$ sudo podman run -d --name hello-world -p 8080:80 docker.io/httpd
List all active Podman container processes and verify that your application is active.
console$ sudo podman ps
Your output should be similar to the one below.
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 16f7b5fdab05 docker.io/library/httpd:latest httpd-foreground 9 seconds ago Up 9 seconds ago 0.0.0.0:8080->80/tcp hello-worldAccess the containerized application using your host port
8080and verify that it's running.console$ curl http://localhost:8080
Output:
<html><body><h1>It works!</h1></body></html>Stop the container.
console$ sudo podman stop hello-world
Login to a Container Registry
Podman supports private and public registries such as the Vultr Container Registry to manage container images. Follow the steps below to create a new Python Flask application, build a container image, and store it in the Vultr Container Registry.
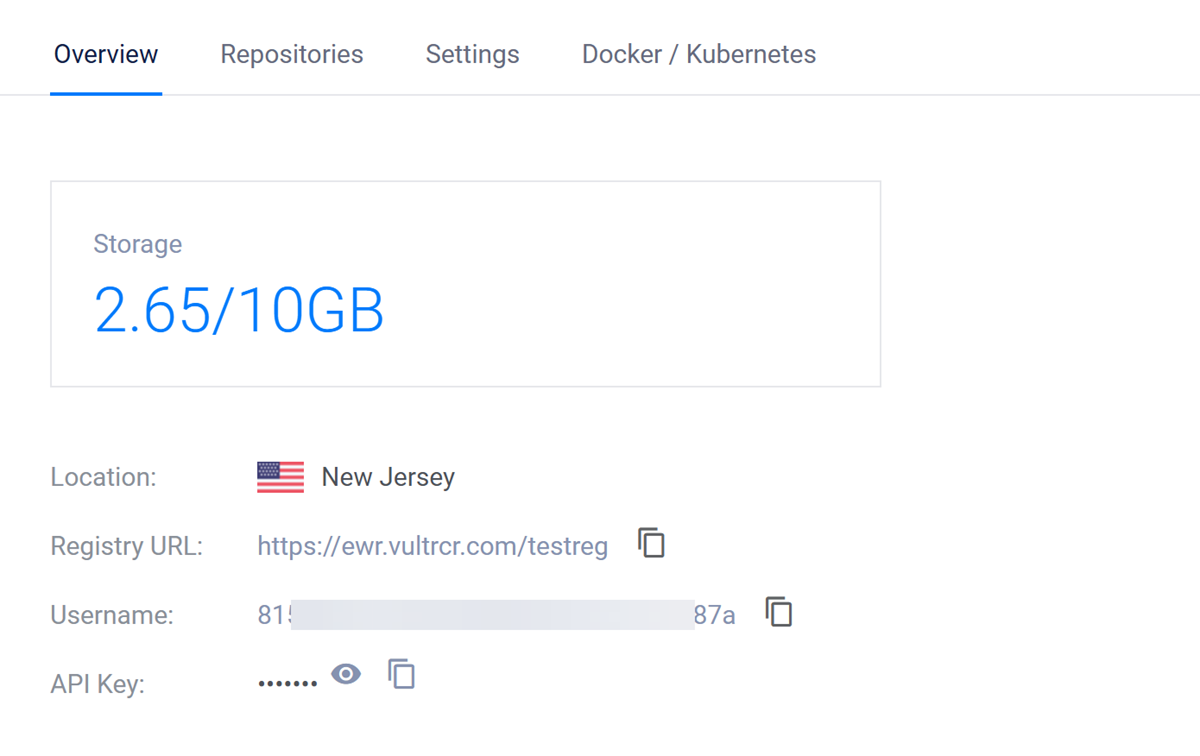
Access your Vultr Container Registry's management page.
Find your registry details within the overview tab, and copy the username and API key credentials to your clipboard.
Create a new environment variable to store your Vultr Container Registry URL. For example,
https://ewr.vultrcr.com/demo.console$ export VULTR_CONTAINER_REGISTRY_NAME=https://ewr.vultrcr.com/demo
Create another environment variable to store your Vultr container registry username. Replace
example-userwith your actual username.console$ export VULTR_CONTAINER_REGISTRY_USERNAME=example-user
Create an environment variable to store your Vultr Container Registry API key. Replace
registry-keywith your actual API key.console$ export VULTR_CONTAINER_REGISTRY_API_KEY=registry-key
Login to the Vultr Container Registry using Podman CLI and the environment variable values.
console$ sudo podman login https://ewr.vultrcr.com/$VULTR_CONTAINER_REGISTRY_NAME -u $VULTR_CONTAINER_REGISTRY_USERNAME -p $VULTR_CONTAINER_REGISTRY_API_KEY
Your output should be similar to the one below when successful.
Login Succeeded!Create a new sample Python application file
app.py.console$ sudo nano app.py
Add the following contents to the file.
pythonfrom flask import Flask app = Flask(__name__) @app.route("/") def hello(): return "Greetings from Vultr" if __name__ == "__main__": app.run(host="0.0.0.0", port=5000)
Save and close the file.
The above Python application initializes a new Flask web server that displays a
Greetings from Vultrprompt when accessed using the application port5000.Create a new Dockerfile to containerize the Python application.
console$ nano Dockerfile
Add the following contents to the file:
dockerfileFROM python:3.9-slim WORKDIR /app COPY . /app RUN pip install flask EXPOSE 5000 CMD ["python", "app.py"]
Save and close the file.
The above Dockerfile configuration builds a new Python Flask application container image with Python 3.9, installs Flask, and runs the application on port
5000.Build the new container image with all files in your working directory.
console$ sudo podman build -t my-python-app .
Your output should be similar to the one below when successful.
//... Successfully tagged localhost/my-python-app:latest a49734b0f695c4c171b15b446c3734e43d27354006fa9bd756af1a78e33d5e47View all container images on your server and verify that the new application image is available.
console$ sudo podman images
Output:
REPOSITORY TAG IMAGE ID CREATED SIZE localhost/my-python-app latest a49734b0f695 9 minutes ago 765 MB docker.io/library/httpd latest b21577b6946f 22 hours ago 152 MBTag the
httpdcontainer image with your desired Vultr Container Registry repository name.console$ sudo podman tag my-python-app ewr.vultrcr.com/$VULTR_CONTAINER_REGISTRY_NAME/my-python-app:v1
List all Podman images again and verify that the tagged image is available.
console$ sudo podman images
Output:
REPOSITORY TAG IMAGE ID CREATED SIZE localhost/my-python-app latest a49734b0f695 9 minutes ago 765 MB ewr.vultrcr.com/demo/my-python-app v1 a49734b0f695 9 minutes ago 765 MB docker.io/library/httpd latest b21577b6946f 22 hours ago 152 MB docker.io/library/python 3.9-slim 724a8ee22b0c 3 months ago 131 MBPush the tagged image to your Vultr Container Registry.
console$ sudo podman push ewr.vultrcr.com/$VULTR_CONTAINER_REGISTRY_NAME/my-python-app:v1
Output:
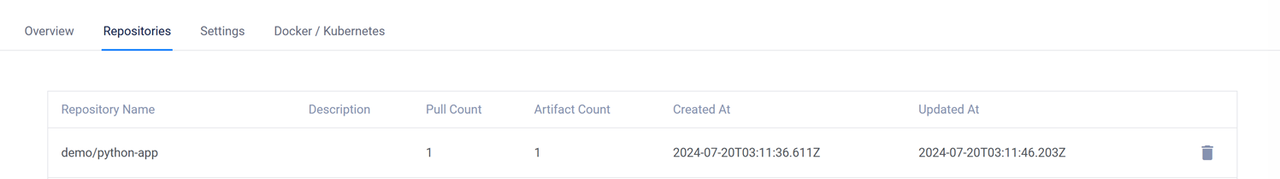
//... Writing manifest to image destination Storing signaturesAccess your Vultr Container Registry's management page, navigate to the Repositories tab, and verify that the new container image repository is available.
Deploy a new application using the container image from your Vultr Container Registry and forward the container port
5000to your localhost port5000.console$ sudo podman run -d --name hello-python -p 5000:5000 ewr.vultrcr.com/$VULTR_CONTAINER_REGISTRY_NAME/my-python-app:v1
Access the localhost port
5000usingcurlto verify that your containerized application is running correctly.console$ curl http://localhost:5000
Output:
Greetings from Vultr
Conclusion
You have installed Podman on your Debian 12 server and managed the containerized application processes. Podman uses container processes similar to Docker and allows you to pull, run, and manage containers on your server. You can integrate Podman with other container development tools using the application API or use custom registries such as the Vultr Container Registry to store your container images. For more information, visit the official Podman documentation.