
Introduction
osTicket is a free and open-source customer support system released under the GPL-2.0 license. This tutorial explains how to install osTicket on CentOS 7 and set up HTTPS with a free Let's Encrypt TLS certificate.
Prerequisites
- A CentOS 7 server with SELinux disabled.
- Follow Vultr's best practices guides to create a sudo user and update the CentOS server.
This tutorial assumes you own a domain name such as example.com, and you have pointed it to the server IP address. If not, replace example.com with the server IP address.
Make sure to replace example.com in the code examples with your domain name or IP address.
1. Install PHP 7.4
CentOS 7 provides PHP version 5.4 in its official repository, but osTicket does not support that version. The recommended version of PHP for osTicket is 7.4. You can install version 7.4 from Remi's RPM repository, a long-time and community-trusted repository for CentOS.
Log in to the server as a non-root sudo user via SSH, then install Remi's RPM repository configuration package.
$ sudo yum install -y https://rpms.remirepo.net/enterprise/remi-release-7.rpmInstall the yum-utils package to configure repositories.
$ sudo yum -y install yum-utilsEnable Remi's RPM repository.
$ sudo yum-config-manager --disable 'remi-php*'
$ sudo yum-config-manager --enable remi-php74Install PHP-FPM and other necessary PHP extensions.
$ sudo yum install -y php-cli php-fpm php-gd php-gettext php-imap php-intl php-json php-mbstring php-xml php-apcu php-mysqli php-opcacheEnable the PHP-FPM service so that PHP-FPM runs at boot time.
$ sudo systemctl enable php-fpm.serviceList all the time zones that your CentOS system supports. Use the Up / Down keys to move through the list, and press Q to exit.
$ timedatectl list-timezonesSelect an appropriate time zone from the list, for example, America/New_York. Then update your CentOS system with that time zone.
$ sudo timedatectl set-timezone America/New_YorkOpen the main PHP configuration file.
$ sudo nano /etc/php.iniFind the line ;date.timezone = and replace it with date.timezone = America/New_York. Then save the configuration file and exit.
To enhance the security of your server, create a dedicated user named osticket as the user/group of PHP-FPM processes for osTicket. This user also owns the osTicket source code files.
$ sudo adduser osticketEvery time you want to add, delete, or update the source code files, you need to switch to this user.
Create the PHP-FPM configuration file from the default one.
$ sudo cp /etc/php-fpm.d/www.conf /etc/php-fpm.d/osticket.confRename the default file to disable it and keep it as a backup.
$ sudo mv /etc/php-fpm.d/www.conf /etc/php-fpm.d/www.conf.defaultOpen the /etc/php-fpm.d/osticket.conf file.
$ sudo nano /etc/php-fpm.d/osticket.confIn the configuration file, any line starting with ; is a comment.
Make sure the listen = 127.0.0.1:9000 setting does not start with ; because PHP-FPM processes listen on the 127.0.0.1 address with the 9000 port.
Search for the following settings, then:
- Replace [www] with [osticket]
- Replace user = apache with user = osticket
- Replace group = apache with group = osticket
- Replace /var/log/php-fpm/www-error.log with /var/log/fpm-php/osticket/error.log
- Replace /var/lib/php/session with /var/lib/php/session.osticket
Save the configuration file and exit.
Create folders to store logs and session data.
$ sudo mkdir -p /var/log/fpm-php/osticket
$ sudo mkdir -p /var/lib/php/session.osticketUpdate the ownership and permissions of the two folders so that only PHP-FPM processes of osTicket can write to them.
$ sudo chown osticket:osticket /var/log/fpm-php/osticket
$ sudo chmod 700 /var/log/fpm-php/osticket
$ sudo chown osticket:osticket /var/lib/php/session.osticket
$ sudo chmod 700 /var/lib/php/session.osticketCheck the new configuration.
$ sudo php-fpm -tStart the PHP-FPM service.
$ sudo systemctl start php-fpm.service2. Install MariaDB 5.5
Although CentOS 7 does not include MySQL in its repository, it includes MariaDB 5.5, a drop-in replacement for MySQL 5.5. Because osTicket supports MySQL 5.5, you can install MariaDB 5.5 for osTicket.
$ sudo yum install -y mariadb-serverEnable the MariaDB service so that MariaDB runs at boot time.
$ sudo systemctl enable mariadb.serviceStart the MariaDB service.
$ sudo systemctl start mariadb.serviceRun the mysql_secure_installation script to improve security and set the password for the MariaDB root user.
$ sudo mysql_secure_installationFor the Enter current password for root (enter for none): question, just press Enter because you have not set a password for the root user.
For the Set root password? [Y/n] question, press Y and Enter to set the root password.
Enter a strong password twice when prompted. You can use a free password manager like KeePassXC or an online tool such as Random Password Generator to generate strong passwords.
Press Y and Enter for any remaining questions to accept the recommended options.
When finished, connect to the MariaDB command line as the root user.
$ sudo mysql -u root -pCreate a MariaDB database named osticket for osTicket.
MariaDB [(none)]> CREATE DATABASE osticket CHARACTER SET utf8mb4 COLLATE utf8mb4_unicode_ci;Create a MariaDB user named osticket for osTicket. Replace password with a strong password.
MariaDB [(none)]> CREATE USER 'osticket'@'localhost' IDENTIFIED BY 'password';
MariaDB [(none)]> GRANT ALL PRIVILEGES ON osticket.* TO 'osticket'@'localhost';
MariaDB [(none)]> FLUSH PRIVILEGES;Exit the MariaDB command line.
MariaDB [(none)]> exit3. Install osTicket
Download the Source Code
Create a folder to store the osTicket source code.
$ sudo mkdir -p /var/www/osticketSet osticket as the owner of the source code folder.
$ sudo chown osticket:osticket /var/www/osticketInstall the git package because you will use it to download the osTicket source code.
$ sudo yum install -y gitSwitch to the osticket user to download and configure osTicket.
$ sudo su osticketDownload the latest of osTicket.
$ cd ~ && git clone https://github.com/osTicket/osTicketDeploy the code into the /var/www/osticket folder you created above.
$ cd osTicket
$ php manage.php deploy --setup /var/www/osticketCreate the configuration file from the sample file.
$ cp /var/www/osticket/include/ost-sampleconfig.php /var/www/osticket/include/ost-config.phpSwitch back to the sudo user to continue with the setup.
$ exit4. Install Nginx
Install Nginx with the following command.
$ sudo yum install -y nginxEnable the Nginx service so that Nginx runs at boot time.
$ sudo systemctl enable nginx.serviceCreate a new configuration file for osTicket.
$ sudo nano /etc/nginx/conf.d/osticket-http.confPaste the following contents:
server {
listen 80;
listen [::]:80;
server_name example.com;
root /var/www/osticket;
index index.php index.html;
location ~ ^/include/ {
deny all;
}
# Pass the PHP script to the FastCGI server listening on 127.0.0.1:9000
# Reference: https://www.nginx.com/resources/wiki/start/topics/examples/phpfcgi/
location ~ [^/]\.php(/|$) {
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
if (!-f $document_root$fastcgi_script_name) {
rewrite ^/api/(.+) /api/http.php/$1 break;
rewrite ^/apps/(.+) /apps/dispatcher.php/$1 break;
rewrite ^/scp/apps/(.+) /scp/apps/dispatcher.php/$1 break;
rewrite ^/pages/(.+) /pages/index.php/$1 break;
return 404;
}
# Mitigate https://httpoxy.org/ vulnerabilities
fastcgi_param HTTP_PROXY "";
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
include fastcgi.conf;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_param PATH_TRANSLATED $document_root$fastcgi_path_info;
}
location ~ ^/(api|apps|pages|scp/apps)/(.+) {
try_files $uri $uri/ @rewrite_rules;
}
location @rewrite_rules {
rewrite ^/api/(.+) /api/http.php/$1 last;
rewrite ^/apps/(.+) /apps/dispatcher.php/$1 last;
rewrite ^/scp/apps/(.+) /scp/apps/dispatcher.php/$1 last;
rewrite ^/pages/(.+) /pages/index.php/$1 last;
}
}Save the configuration file and exit. Then check the new configuration.
$ sudo nginx -tStart the Nginx service.
$ sudo systemctl start nginx.serviceUpdate the firewall to allow incoming HTTP requests.
$ sudo firewall-cmd --permanent --zone=public --add-service=httpReload the current firewall session.
$ sudo firewall-cmd --reload5. (Optional) Configure HTTPS
If you own a valid domain name, you can set up HTTPS for your osTicket at no cost. Using the Certbot program, you can get a free TLS certificate from Let's Encrypt, a certificate authority.
Install Certbot with Snap
Snap Store is an app store for Linux with millions of users. It makes it easy to get the latest version of Certbot with features like automatic certificate renewal. The package that provides everything you need to work with the Snap Store is snapd.
Install the snapd package.
$ sudo yum install snapd -yEnable the snapd service.
$ sudo systemctl enable --now snapd.socketEnable classic snap support.
$ sudo ln -s /var/lib/snapd/snap /snapGet the latest version of snapd core.
$ sudo snap install core && sudo snap refresh coreDo not worry if you get the following error.
error: too early for operation, device not yet seeded or device model not acknowledgedAfter installing snapd, it may take a little while to initialize its environment. Please wait a while before retrying the above command.
Install Certbot.
$ sudo snap install --classic certbotMake the certbot command globally available.
$ sudo ln -s /snap/bin/certbot /usr/bin/certbotGet a Let's Encrypt Certificate
Rename the HTTP configuration file to make it the template for the HTTPS configuration file.
$ sudo mv /etc/nginx/conf.d/osticket-http.conf /etc/nginx/conf.d/osticket-https.tplCreate a new configuration file to serve HTTP requests.
$ sudo nano /etc/nginx/conf.d/osticket-http.confPaste the following contents:
server {
listen 80;
listen [::]:80;
server_name example.com;
root /var/www/osticket;
location / {
return 301 https://$server_name$request_uri;
}
location /.well-known/acme-challenge/ {}
}This configuration makes Nginx redirect all HTTP requests, except those from Let's Encrypt, to corresponding HTTPS requests.
Save the configuration file and exit. Then check the Nginx configuration.
$ sudo nginx -tApply the new configuration.
$ sudo systemctl reload nginx.serviceNow you can run the following command to get the Let's Encrypt certificate.
$ sudo certbot certonly --webroot -w /var/www/osticket -d example.com -m admin@example.com --agree-tosYou may need to answer a question about sharing your email with the Electronic Frontier Foundation.
When finished, certbot tells you the path of your certificate file and key file:
/etc/letsencrypt/live/example.com/fullchain.pem
/etc/letsencrypt/live/example.com/privkey.pemAnother critical file, located in the same folder, also needed for the next step, is chain.pem.
Install the Certificate with Nginx
Generate a file with DH parameters for DHE ciphers.
$ sudo openssl dhparam -out /etc/nginx/dhparam.pem 20482048 is the recommended size of DH parameters. This process may take a while, so please be patient.
Create the HTTPS configuration file from the template file above.
$ sudo mv /etc/nginx/conf.d/osticket-https.tpl /etc/nginx/conf.d/osticket-https.confOpen the HTTPS configuration file.
$ sudo nano /etc/nginx/conf.d/osticket-https.confFind the following lines:
listen 80;
listen [::]:80;Replace them with:
listen 443 ssl http2;
listen [::]:443 ssl http2;
ssl_certificate /etc/letsencrypt/live/example.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/example.com/privkey.pem;
ssl_session_timeout 1d;
ssl_session_cache shared:MozSSL:10m; # about 40000 sessions
# DH parameters file
ssl_dhparam /etc/nginx/dhparam.pem;
# intermediate configuration
ssl_protocols TLSv1.2;
ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384;
ssl_prefer_server_ciphers off;
# HSTS (ngx_http_headers_module is required) (63072000 seconds)
#
# Uncomment the following line only if your website fully supports HTTPS
# and you have no intention of going back to HTTP, otherwise, it will
# break your site.
#
# add_header Strict-Transport-Security "max-age=63072000" always;
# OCSP stapling
ssl_stapling on;
ssl_stapling_verify on;
# verify chain of trust of OCSP response using Root CA and Intermediate certs
ssl_trusted_certificate /etc/letsencrypt/live/example.com/chain.pem;
# Use Cloudflare DNS resolver
resolver 1.1.1.1;Save the configuration file and exit. Then check the Nginx configuration.
$ sudo nginx -tApply the new configuration.
$ sudo systemctl reload nginx.serviceUpdate the firewall to allow incoming HTTPS requests.
$ sudo firewall-cmd --permanent --zone=public --add-service=httpsReload the current firewall session.
$ sudo firewall-cmd --reloadAutomate Renewal
Let's Encrypt certificates are valid for 90 days, so you must renew your TLS certificate at least once every three months. The Certbot installation automatically created a systemd timer unit to automate this task. Run the following command to verify the timer is active.
$ sudo systemctl list-timers | grep 'certbot\|ACTIVATES'After renewing the certificate, Certbot will not automatically reload Nginx, so Nginx still uses the old certificate. You must write a script inside the /etc/letsencrypt/renewal-hooks/deploy folder to reload Nginx.
Open your text editor.
$ sudo nano /etc/letsencrypt/renewal-hooks/deploy/reload-nginx.shPaste the following contents:
#!/bin/bash
/usr/bin/systemctl reload nginx.serviceSave and exit. Then make the script executable.
$ sudo chmod +x /etc/letsencrypt/renewal-hooks/deploy/reload-nginx.shTest the renewal process with a dry run.
$ sudo certbot renew --dry-runThis Vultr article explains all the above steps in more detail. This kind of TLS setup gives you an A on the SSL Labs test.
6. Complete the osTicket Setup
Restart the server to make sure it still works afterward.
$ sudo rebootWait a moment for the system to boot, then open the http://example.com link in your browser. The osTicket Installer screen appears, and you see that your server configuration meets all the minimum requirements.
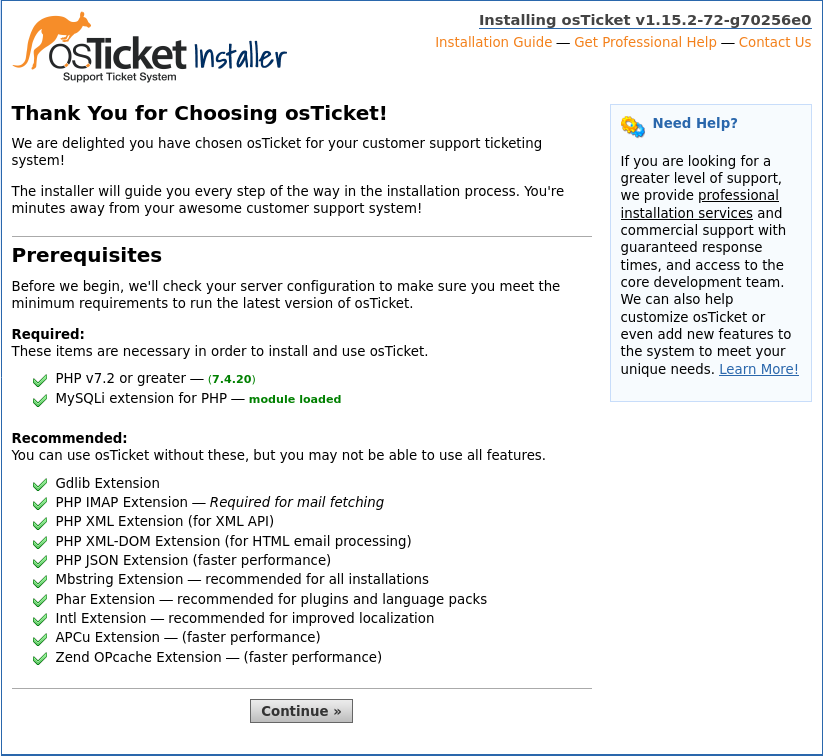
Click the Continue button to move to the osTicket Basic Installation screen.
Fill out the form with your information to update the System Settings and create the Admin User.
For Database Settings, enter osticket into the MySQL Database and MySQL Username fields, then enter the password of the osticket user you created in step 2 into the MySQL Password field.
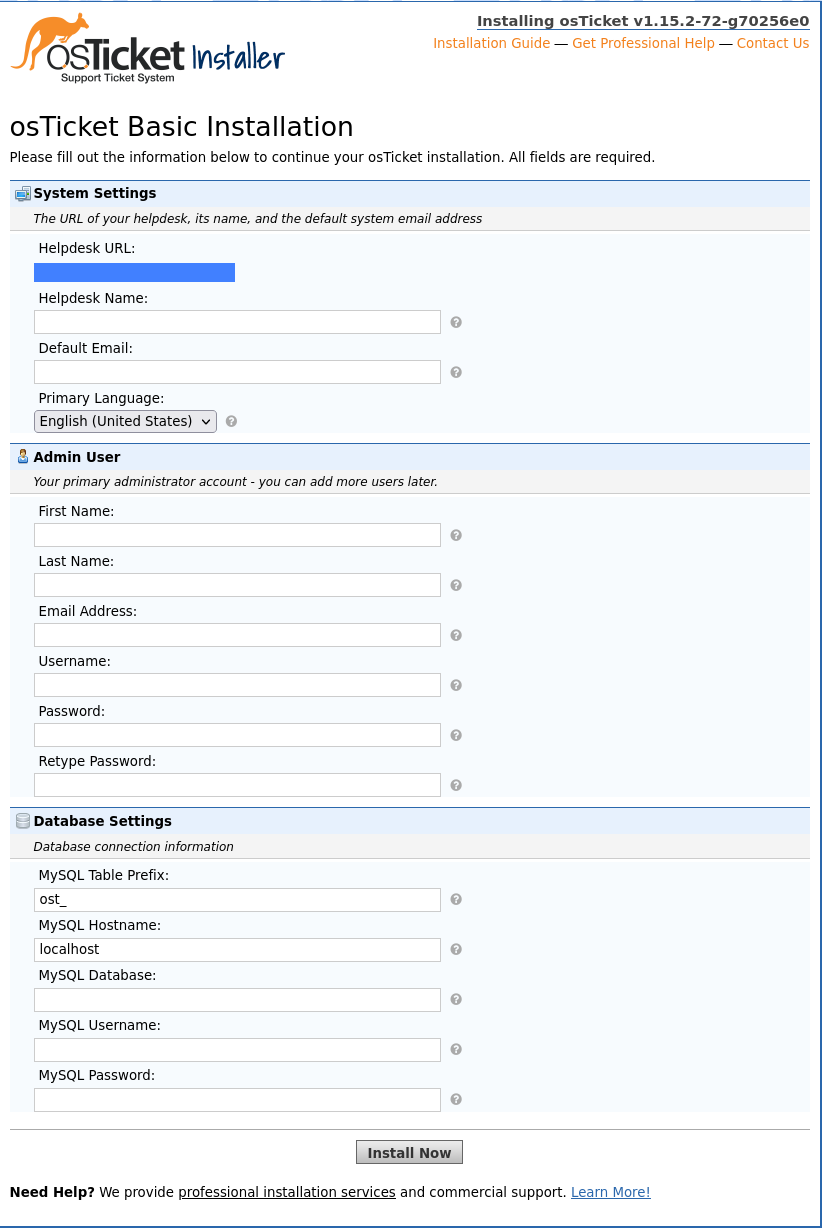
Click the Install Now button to install osTicket. When finished, it redirects you to the Congratulations screen.
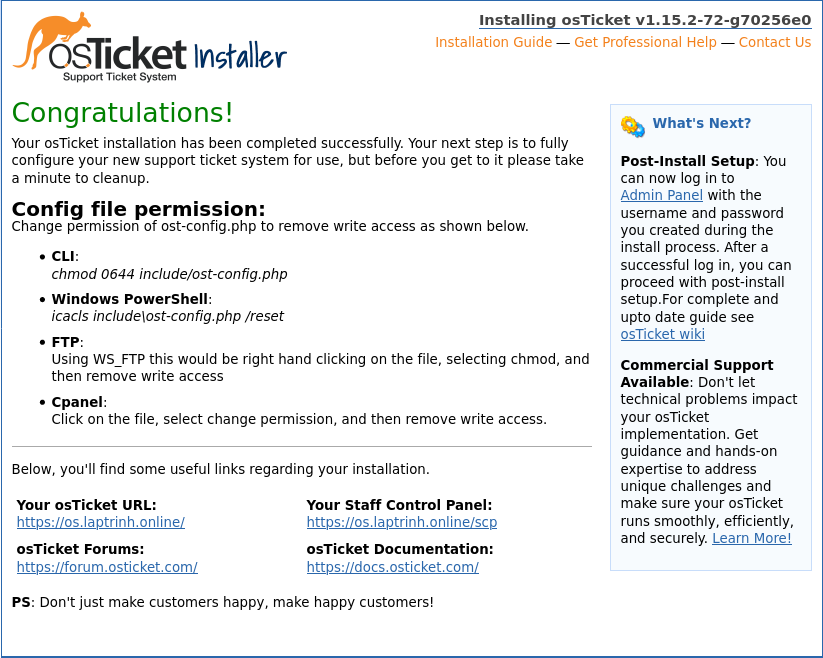
Go back to your SSH session to clean up by deleting the setup folder.
$ sudo rm -rf /var/www/osticket/setupSet root as the owner of the osTicket configuration file to prevent PHP-FPM from changing it.
$ sudo chown root:root /var/www/osticket/include/ost-config.phpYour osTicket website is now ready. You should open the Staff Control Panel page, https://example.com/scp/, to proceed with the post-install setup. For complete and up-to-date instructions, read the Post-Install Setup Guide of the osTicket documentation.
No comments yet.