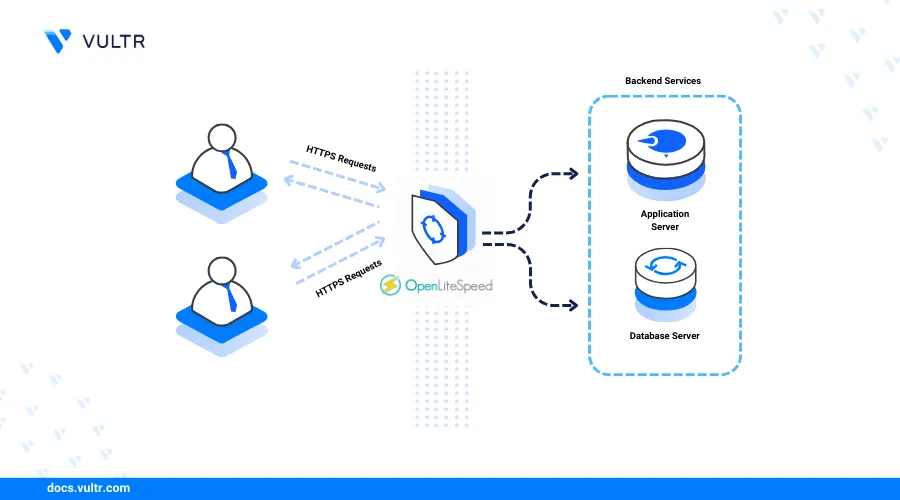
Introduction
Install OpenLiteSpeed on FreeBSD 14 to leverage a high-performance, open-source webserver designed for low resource consumption. OpenLiteSpeed features an event-driven architecture, built-in caching, and a user-friendly web-based administration interface. It supports modern web technologies, including HTTP/2, HTTP/3, QUIC, and Brotli compression, making it an efficient and powerful solution for hosting dynamic web applications.
This article explains how to install OpenLiteSpeed on FreeBSD 14 and configure the webserver to serve web applications using virtual host configurations.
Build and Install OpenLiteSpeed on FreeBSD 14 From Source
OpenLiteSpeed is not available in the default package repositories and ports collection on FreeBSD. Follow the steps below to build and install OpenLiteSpeed on a FreeBSD server from source.
Update the server's package index.
console$ sudo pkg update
Install all required dependencies for building OpenLiteSpeed.
console$ sudo pkg install -y git cmake gcc gmake go pkgconf autoconf automake libtool pcre pcre2 wget nano modsecurity3 sudo
Build and Install the YAJL Dynamic Library
Yet Another JSON Library (YAJL) is a lightweight, and highly portable JSON parsing and generation library written in C. OpenLiteSpeed requires YAJL to install and run dynamic libraries. Follow the steps below to build and install the YAJL dynamic library.
Create the
/usr/local/srcdirectory to store your project files.console$ sudo mkdir /usr/local/src
Switch to the
/usr/local/srcdirectory.console$ cd /usr/local/src
Clone the YAJL repository using Git.
console$ sudo git clone https://github.com/lloyd/yajl.git
Switch to the cloned
yajldirectory.console$ cd yajl
Checkout to the latest YAJL stable release using Git. For example,
2.1.0.console$ sudo git checkout 2.1.0
Create a new
builddirectory.console$ sudo mkdir build
Switch to the
builddirectory.console$ cd build
Run the following
cmakecommand to build YAJL as a dynamic library.console$ sudo cmake -DCMAKE_INSTALL_PREFIX=/usr/local \ -DCMAKE_POSITION_INDEPENDENT_CODE=ON \ -DCMAKE_C_FLAGS="-fPIC" \ -DCMAKE_CXX_FLAGS="-fPIC" \ ..
Use the
make installcommand to install the YAJL library.console$ sudo make install
List all files in the
/usr/local/lib/libyajl.*directory to verify that YAJL is installed.console$ sudo ls /usr/local/lib/libyajl.*
Update the system's dynamic linker cache to read shared libraries in the
/usr/local/libdirectory.console$ sudo ldconfig -v -m /usr/local/lib
Create a
LDFLAGSenvironment variable to enable OpenLiteSpeed to access all required libraries.console$ export LDFLAGS="-L/usr/local/lib"
Create a
CPPFLAGSenvironment variable to enable thegcccompiler to access dependency libraries.console$ export CPPFLAGS="-I/usr/local/include"
If you are using Debian 12, you can follow this guide to install OpenLiteSpeed on Debian 12 and set up a high-performance, lightweight webserver with support for modern web technologies.
Build and Install OpenLiteSpeed
Follow the steps below to build and install OpenLiteSpeed on FreeBSD after setting up all necessary libraries including YAJL on the server.
Switch to the
/usr/local/srcdirectory.console$ cd /usr/local/src
Clone the OpenLiteSpeed repository.
console$ sudo git clone https://github.com/litespeedtech/openlitespeed.git
Switch to the
openlitespeeddirectory.console$ cd openlitespeed
Checkout to the latest stable release. For example,
1.8.2.console$ sudo git checkout tags/v1.8.2
Update all submodules using Git.
console$ sudo git submodule update --init
Open the
/usr/local/src/openlitespeed/src/extensions/cgi/lscgid.cppfile using a text editor such asnano.console$ nano /usr/local/src/openlitespeed/src/extensions/cgi/lscgid.cpp
Add the following
#define LS_NS_LEN 5preprocessor directive after the***comments in the file.cpp* * * You should have received a copy of the GNU General Public License * * along with this program. If not, see http://www.gnu.org/licenses/. * *****************************************************************************/ #define LS_NS_LEN 5
Save and close the file.
The above
#define LS_NS_LEN 5preprocessor directive enables the CGI module namespace used for unique process identification tasks. Ensure that the directive includes the#symbol to work correctly on your server. Setting the directive's value to5enables compatibility with other system processes and prevents namespace collisions.Use the
ldconfigcommand to apply the configuration changes.console$ sudo ldconfig -v -m /usr/local/lib
Run the
build.shscript to build OpenLiteSpeed.console$ sudo ./build.sh
Wait for at least 15 minutes for the build process to complete.
Run the
install.shscript to install OpenLiteSpeed.console$ sudo ./install.sh
When the installation is successful, note the default administrator password in your output similar to the one below.
SSL host is [webadmin], use adminSSL 2024-12-02 14:15:12 URL:http://www.litespeedtech.com/packages/lsphp5_bin/x86_64-freebsd/lsphp5 [4651136/4651136] -> "/usr/local/lsws/ ........................................ Your webAdmin password is Wz5hzwGM, written to file /usr/local/lsws/adminpasswd. You must reboot the server to ensure the settings change take effect!Reboot the server to apply all OpenLiteSpeed changes.
console$ sudo reboot
Start the OpenLiteSpeed webserver.
console$ sudo /usr/local/lsws/bin/lswsctrl start
Output:
[OK] litespeed: pid=897.Access port
8088using your server's IP address in a web browser such as Chrome and verify that the default OpenLiteSpeed page displays.http://SERVER-IP:8088
Stop the OpenLiteSpeed webserver to set it up as a system service.
console$ sudo /usr/local/lsws/bin/lswsctrl stop
If you are using Ubuntu Server, install OpenLiteSpeed on Ubuntu 24.04 to configure a lightweight, high-performance webserver with support for HTTP/3 and built-in caching.
Set Up OpenLiteSpeed as a System Service
Follow the steps below to set up the OpenLiteSpeed webserver as a system service to automatically start on the server.
Create a new
/usr/local/etc/rc.d/openlitespeedfile.console$ sudo nano /usr/local/etc/rc.d/openlitespeed
Add the following configurations to the file.
sh#!/bin/sh # PROVIDE: openlitespeed # REQUIRE: LOGIN # KEYWORD: shutdown . /etc/rc.subr name="openlitespeed" desc="OpenLiteSpeed webserver" rcvar="${name}_enable" load_rc_config $name : ${openlitespeed_enable:="NO"} : ${openlitespeed_user:="nobody"} pidfile="/usr/local/lsws/admin/tmp/admin.pid" command="/usr/local/lsws/bin/lswsctrl" start_cmd="openlitespeed_start" stop_cmd="openlitespeed_stop" status_cmd="openlitespeed_status" openlitespeed_start() { echo "Starting ${name}." /usr/local/lsws/bin/lswsctrl start } openlitespeed_stop() { echo "Stopping ${name}." /usr/local/lsws/bin/lswsctrl stop } openlitespeed_status() { /usr/local/lsws/bin/lswsctrl status } run_rc_command "$1"
Save and close the file.
Enable
executepermissions on the script.console$ sudo chmod +x /usr/local/etc/rc.d/openlitespeed
Open the
/etc/rc.conffile.console$ sudo nano /etc/rc.conf
Add the following directive to the
rc.conffile to enable the OpenLiteSpeed service to automatically start at boot.iniopenlitespeed_enable="YES"
Start the OpenLiteSpeed system service.
console$ sudo service openlitespeed start
View the OpenLiteSpeed service status and verify that it's running.
console$ sudo service openlitespeed status
Secure the OpenLiteSpeed Webserver
OpenLiteSpeed generates a default administrator password during installation and serves the web administration interface on port 7080 using HTTP. Follow the steps below to reset the default administrator password, generated trusted SSL certificates using a domain and configure the packet filter (pf) firewall to secure connections to the OpenLiteSpeed webserver.
Run the
admpass.shscript to reset the OpenLiteSpeed administrator password.console$ sudo /usr/local/lsws/admin/misc/admpass.sh
Enter a new administrator username or press Enter to use the default
adminusername.Please specify the user name of administrator. This is the user name required to login the administration Web interface. User name [admin]:Enter a strong administrator password when prompted.
Please specify the administrator's password. This is the password required to login the administration Web interface. Password: Retype password:Output:
Administrator's username/password is updated successfully!
Search the
pkgrepository to verify the available Certbot Let's Encrypt client package version.console$ sudo pkg search certbot
Output:
py311-certbot-2.11.0,1 Let's Encrypt client py311-certbot-apache-2.11.0 Apache plugin for Certbot ......................................... py311-certbot-nginx-2.11.0 NGINX plugin for CertbotInstall Certbot depending on the available version.
console$ sudo pkg install py311-certbot
Use Certbot to generate a new Let's Encrypt SSL certificate using your virtual host domain. Replace
app.example.comwith your actual domain andadmin@example.comwith your active email address.console$ sudo certbot certonly --standalone -d app.example.com -d www.app.example.com --agree-tos
Open the
/etc/rc.conffile.console$ sudo nano /etc/rc.conf
Add the following directives at the end of the
/etc/rc.conffile.inipf_enable="YES" pf_rules="/etc/pf.conf" pf_flags="" pflog_enable="YES" pflog_logfile="/var/log/pflog"
Save and close the file.
The above configuration enables the packet filter firewall to automatically start at boot with the following options:
pf_enable="YES": Enables the packet filter firewall.pf_rules="/etc/pf.conf": Sets/etc/pf.confas the active firewall configuration.pflog_enable="YES": Enables firewall logging.
View all network interfaces and note the main interface name to use in the firewall configuration.
console$ ifconfigOutput:
vtnet0: flags=1008843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST,LOWER_UP> metric 0 mtu 1500 options=4c00ba<TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWTSO,LINKSTATE,TXCSUM_IPV6> ether 56:00:05:2b:05:0c inet 192.0.2.100 netmask 0xfffffe00 broadcast 192.0.2.255 media: Ethernet autoselect (10Gbase-T <full-duplex>) status: active nd6 options=29<PERFORMNUD,IFDISABLED,AUTO_LINKLOCAL> lo0: flags=1008049<UP,LOOPBACK,RUNNING,MULTICAST,LOWER_UP> metric 0 mtu 16384 options=680003<RXCSUM,TXCSUM,LINKSTATE,RXCSUM_IPV6,TXCSUM_IPV6> inet 127.0.0.1 netmask 0xff000000 inet6 ::1 prefixlen 128 inet6 fe80::1%lo0 prefixlen 64 scopeid 0x2 groups: lo nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>vtnet0is the public network interface name with the IP address192.0.2.100based on the above output.Create the
/etc/pf.conffirewall configuration file.console$ sudo nano /etc/pf.conf
Add the following configurations to the
/etc/pf.conffile.iniext_if = "vtnet0" set block-policy drop set loginterface $ext_if set skip on lo0 nat on $ext_if from !($ext_if:network) to any -> ($ext_if) # Rules # Required to maintain current ssh connection active pass out on $ext_if proto tcp from port 22 to any flags any # Allow inbound SSH, HTTP, and HTTPS pass in quick on $ext_if proto tcp to port {22 80 443 8088 7080} keep state # Allow SSH, HTTP, HTTPS # Default block rule block in all # Allow all outbound traffic pass out all keep state
Save and close the file.
The above firewall configuration enables network connections to the following ports on the server:
22: SSH connections port.80: HTTP port.443: HTTPS port.8088: The default OpenLiteSpeed virtual host port.7080: The OpenLiteSpeed web administration port.
Test the
/etc/pf.conffile for configuration errors.console$ sudo pfctl -nf /etc/pf.conf
Start the packet filter firewall.
console$ sudo service pf start
The above command may temporarily block your active SSH connection. Ensure to reconnect to the server when the firewall starts.
View the firewall status and verify that it's active.
console$ pfctl -s info
Output:
Status: Enabled for 0 days 00:00:51 Debug: Urgent Interface Stats for vtnet0 IPv4 IPv6 Bytes In 13731 128 Bytes Out 12094 468 Packets In Passed 108 6 Blocked 17 0 Packets Out Passed 0 0 Blocked 1 0
Create a Virtual Host Configuration
A virtual host configuration enables OpenLiteSpeed to serve web applications and services using a specific domain or address on your server. Follow the steps below to create a new OpenLiteSpeed virtual host configuration using your domain and serve a custom HTML web application on the server.
Navigate to the OpenLiteSpeed virtual host configurations directory.
console$ sudo cd /usr/local/lsws/conf/vhosts
Create a new
app.example.comvirtual host directory.console$ sudo mkdir -p app.example.com
Create a new
htmlsubdirectory in theapp.example.comdirectory to store the web application files.console$ sudo mkdir -p app.example.com/html
Grant the
lsadmOpenLiteSpeed user ownership privileges to the directory.console$ sudo chown -R lsadm:nobody app.example.com
Switch to the
app.example.com/htmldirectory.console$ sudo cd app.example.com/html
Run the following command to create a new
index.htmlweb application file to display aGreetings from Vultrmessage.console$ echo "<h1 align='center'> Greetings from Vultr </h1>" | sudo tee /usr/local/lsws/conf/vhosts/app.example.com/index.html
Set Up the Virtual Host Information in the OpenLiteSpeed Web Administration Dashboard
Follow the steps below to set up the virtual host information using the OpenLiteSpeed web administration dashboard.
Access port
7080using your server's IP address to log in to the OpenLiteSpeed web administration dashboard.http://SERVER-IP:7080Enter the OpenLiteSpeed administrator credentials you created earlier to log in.
Click Virtual Hosts in the OpenLiteSpeed dashboard.
Click + within the Virtual Host List section to set up a new virtual host.
Add the following virtual host information to the respective fields.
- Virtual Host Name:
app.example.com - Virtual Host Root:
$SERVER_ROOT/conf/vhosts/app.example.com/ - Config File:
conf/vhosts/app.example.com/vhconf.conf - Follow Symbolic Link:
Yes - Enable Scripts/ExtApps:
Yes - Restrained:
Yes - External App Set UID Mode:
Server UID
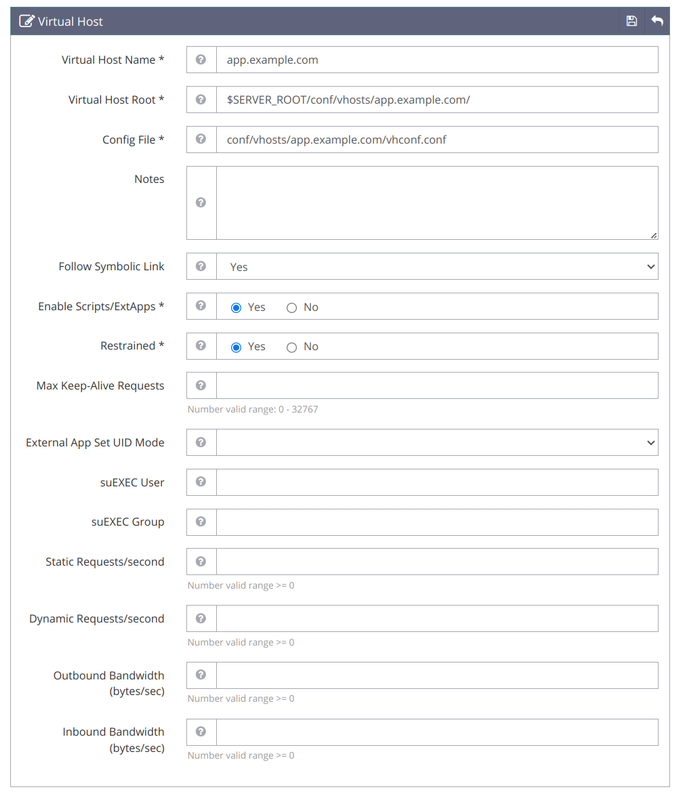
- Virtual Host Name:
Click Save and click the CLICK TO CREATE option when prompted to create the virtual host configuration.
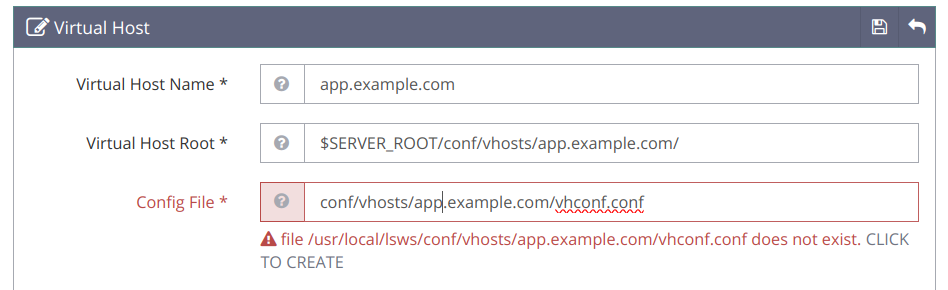
Click Save to apply the virtual host configuration changes.
Click the virtual host to open its management page.
Navigate to the General tab and modify the virtual host configuration with the following information.
- Document Root:
$VH_ROOT/html/ - Domain Name:
app.example.com - Domain Aliases:
app.example.com - Enable GZIP Compression:
Yes - Enable Brotli Compression:
Yes
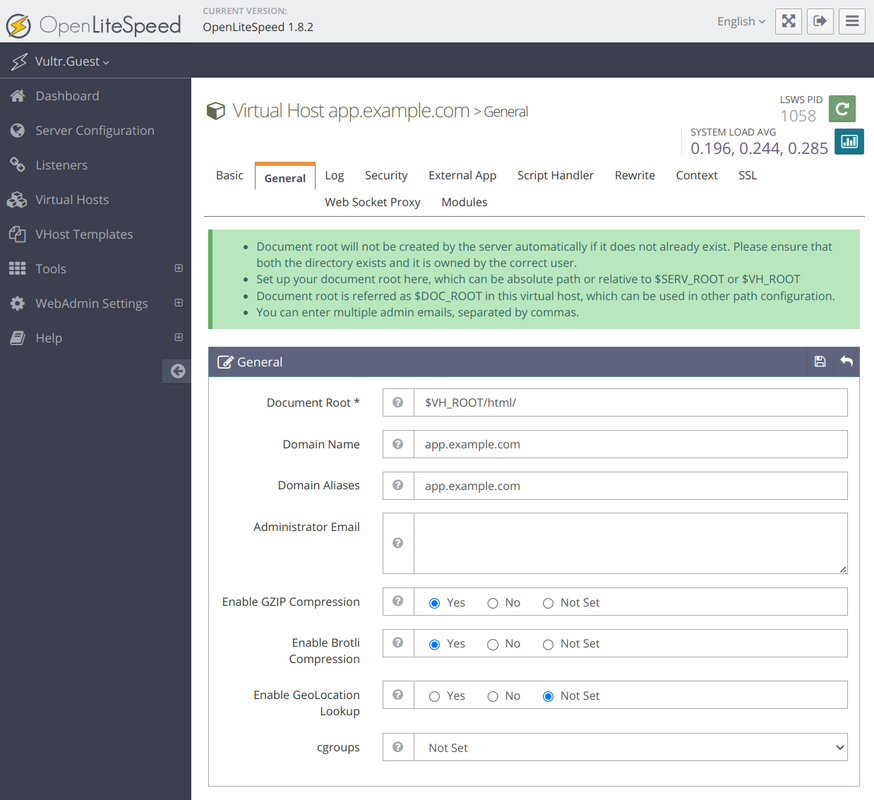
- Document Root:
Click Save to apply the virtual host changes.
Click Listeners on the main navigation menu.
Click + to set up a new listener with the following details:
- Listener Name:
app.example.com - IP Address:
Any IPv4 - Port:
80 - Secure:
No
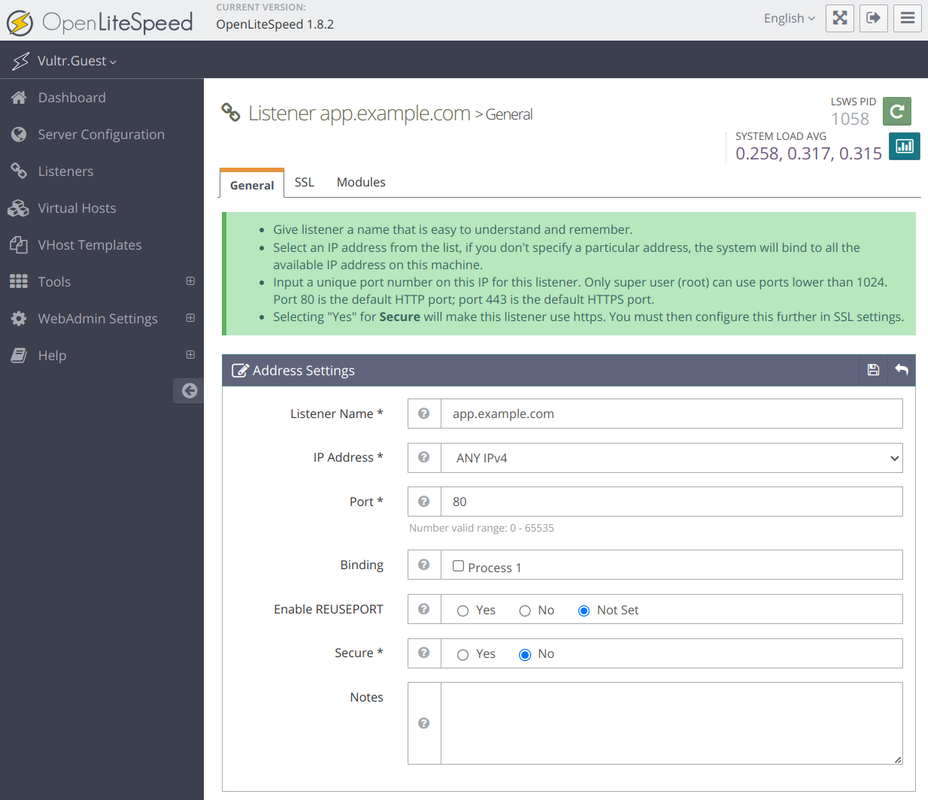
- Listener Name:
Click Save to apply the listener configuration.
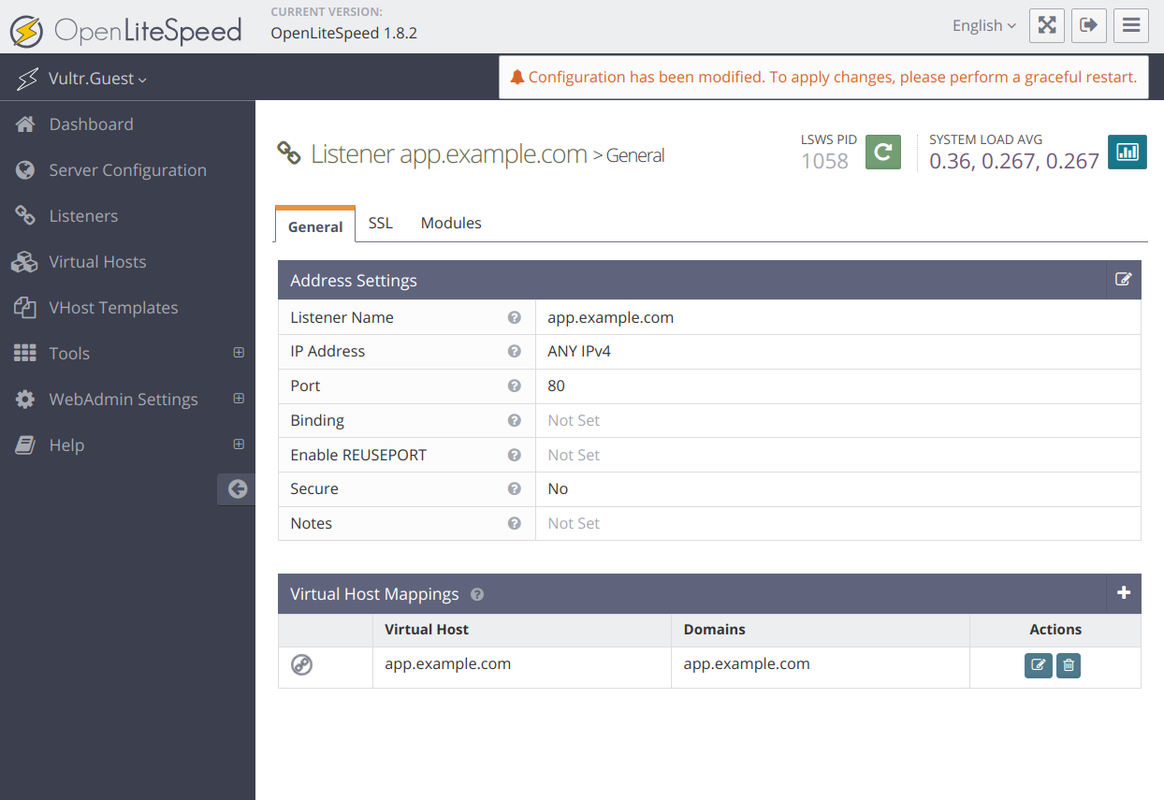
Scroll to the Virtual Host Mappings section and click + to create a new configuration map.
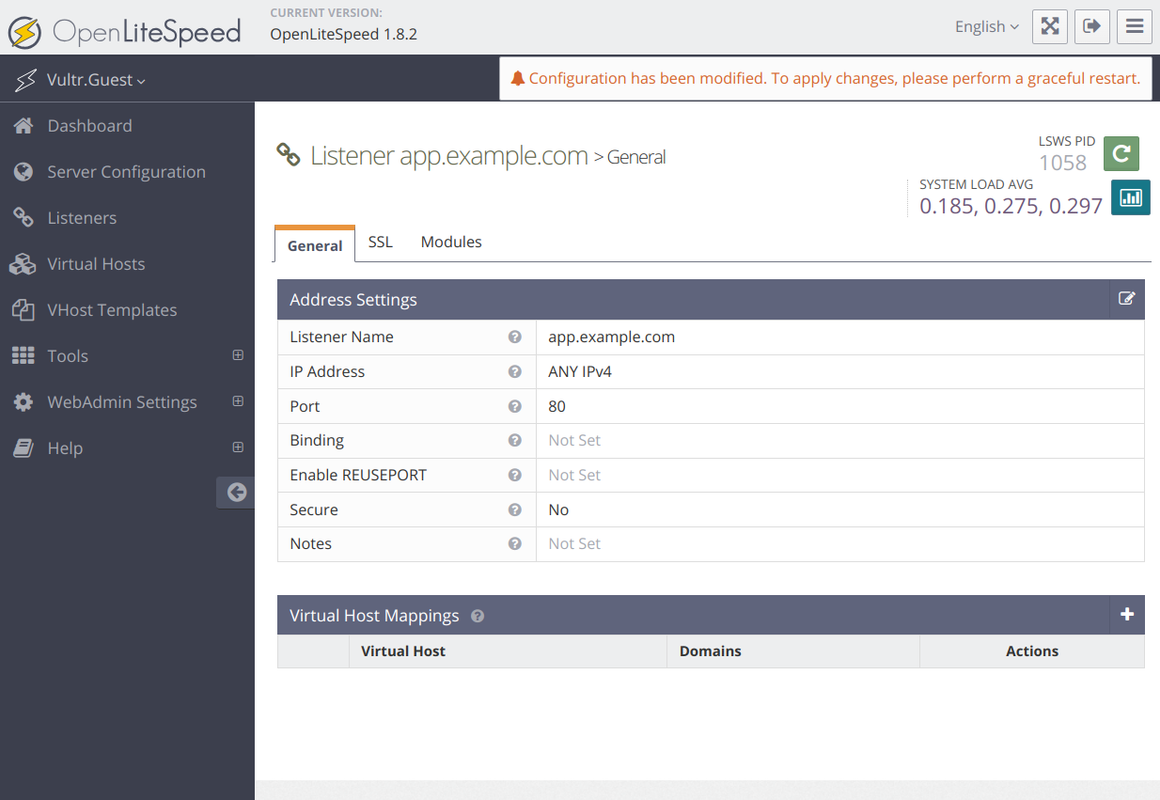
Enter the following details to map the listener to a virtual host configuration.
- Virtual Host:
app.example.com - Domains:
app.example.com
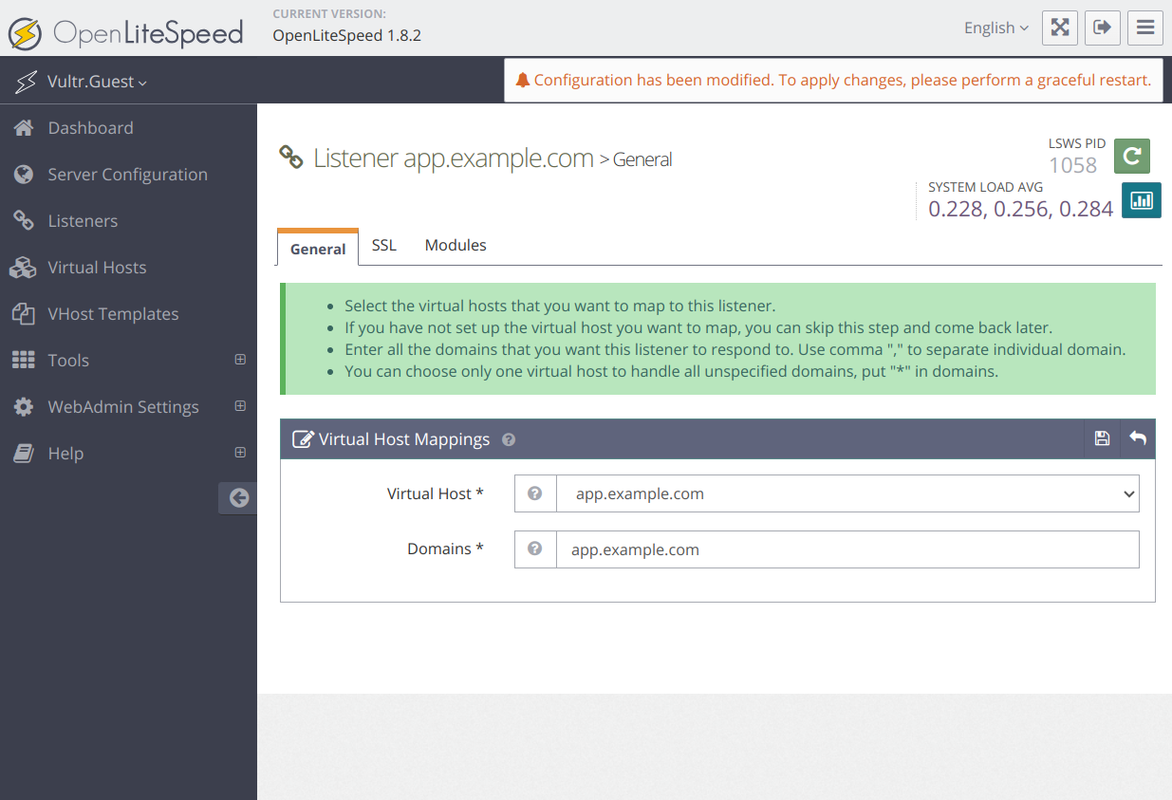
- Virtual Host:
Click Save to apply the listener configuration.
Enable Secure HTTPS Connections
Follow the steps below to enable secure HTTPS connections to the virtual host using the Let's Encrypt SSL certificates you generated earlier.
Navigate to Listeners page and create a new listener with the following information:
- Listener Name:
app.example.com.https - IP Address:
ANYIPv4 - Port:
443 - Secure:
Yes
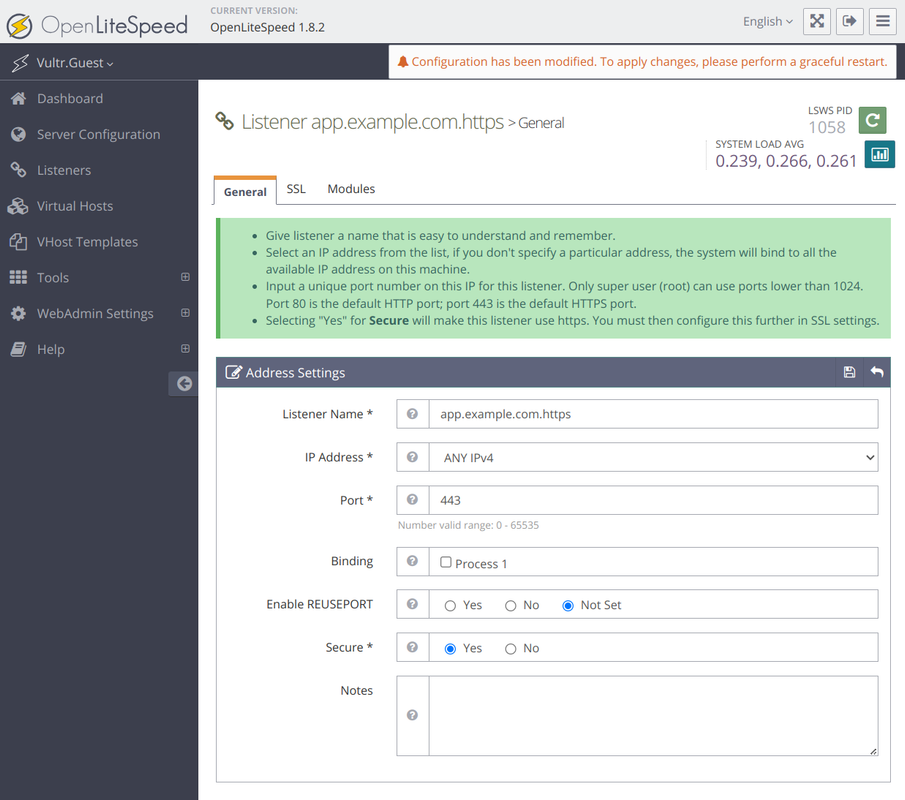
- Listener Name:
Navigate to the Virtual Host Mappings section and map your virtual host configuration with the following details:
- Virtual Host:
app.example.com - Domains:
app.example.com
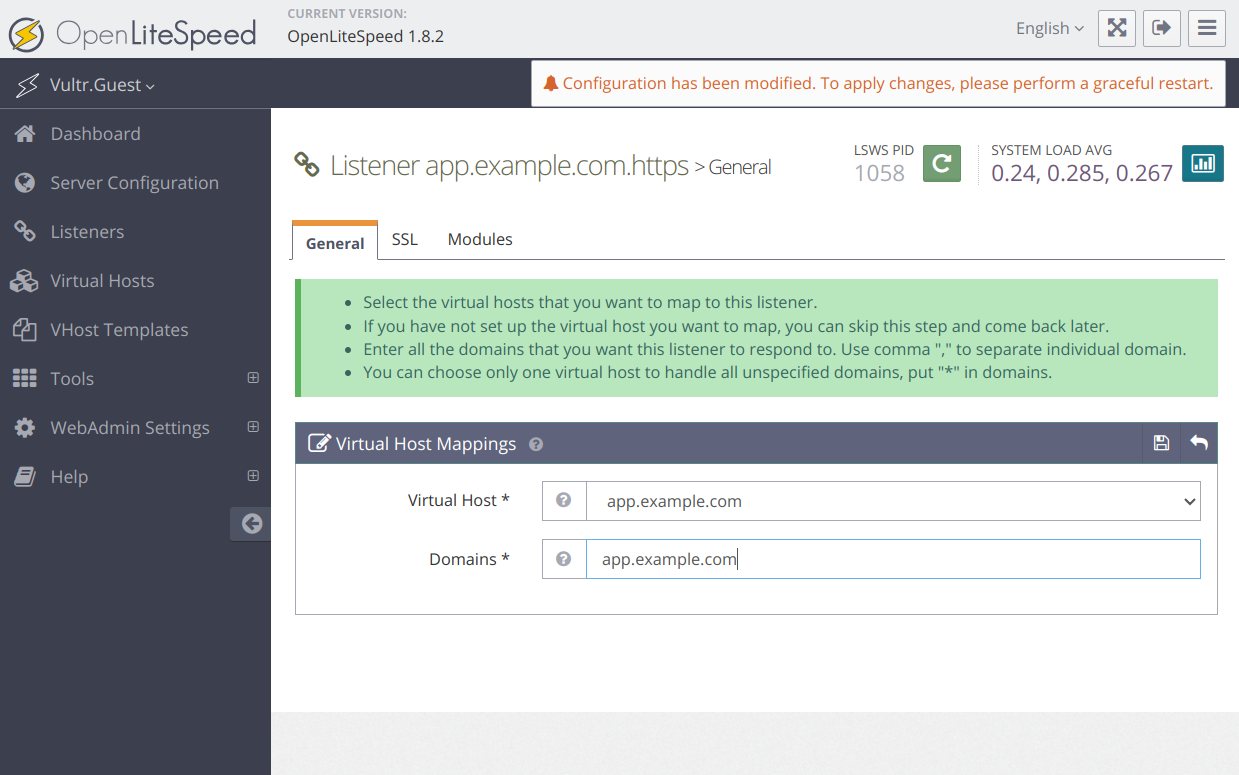
- Virtual Host:
Click Save to apply the listener configuration.
Open the listener's configuration page and navigate to the SSL tab.
Enter the following Let's Encrypt SSL certificate paths to apply to your virtual host domain configuration.
- Private Key File:
/usr/local/etc/letsencrypt/live/app.example.com/privkey.pem - Certificate File:
/usr/local/etc/letsencrypt/live/app.example.com/fullchain.pem - Chained Certificate:
Yes
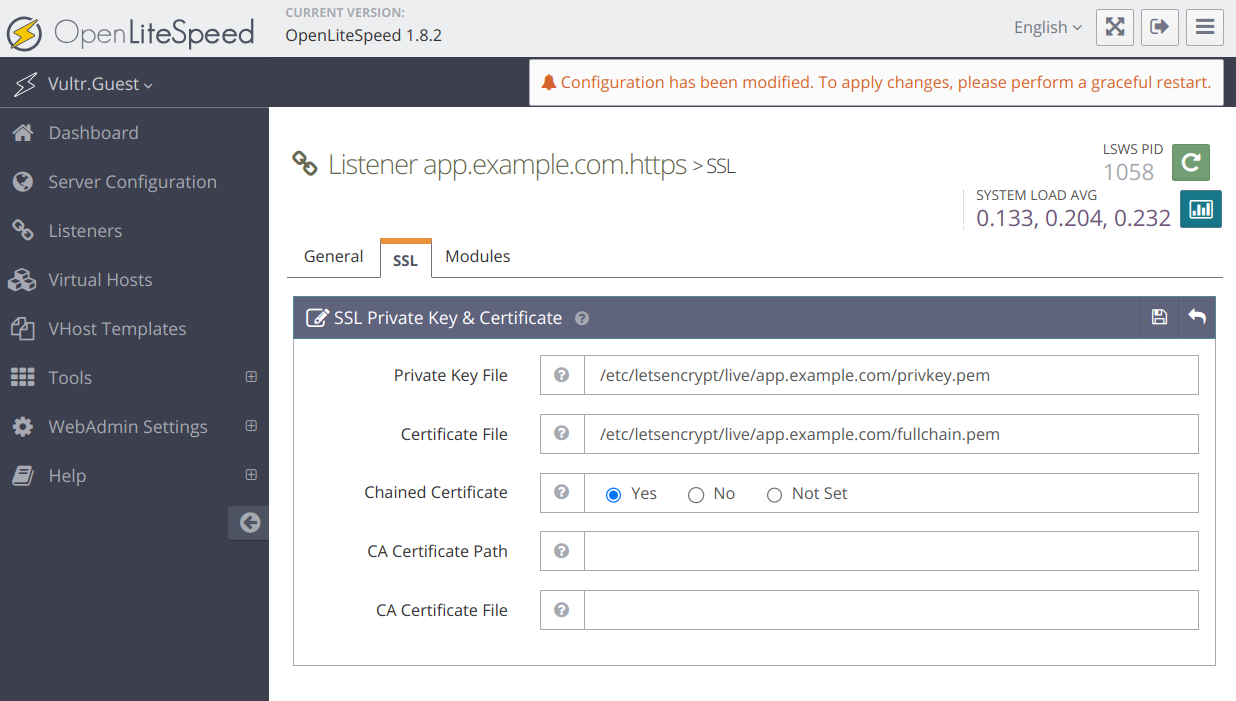
- Private Key File:
Click Save to apply the virtual host listener configuration changes.
Access your
app.example.comvirtual host domain in a new web browser window and verify that theGreetings from Vultrprompt displays.https://app.example.com
Conclusion
You have installed OpenLiteSpeed on FreeBSD 14 from source code and enabled the webserver to automatically start at boot. You can create multiple virtual host configurations and listeners to deliver web applications on the server. For more webserver configuration options, please visit the OpenLiteSpeed documentation.